108 lines
3.5 KiB
Markdown
108 lines
3.5 KiB
Markdown
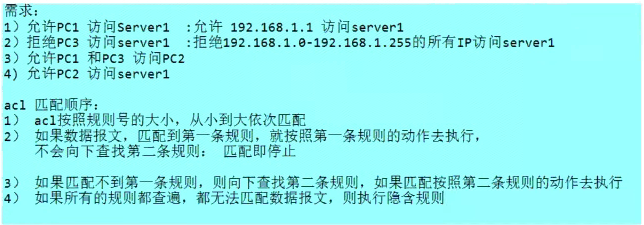
# ACL规则优先级
|
||
|
||

|
||
|
||
|
||
|
||
### 一、IP
|
||
|
||
- AR1
|
||
|
||
```
|
||
[AR1]int g0/0/0
|
||
[AR1-GigabitEthernet0/0/0]ip add 192.168.3.254 24
|
||
[AR1-GigabitEthernet0/0/0]int g0/0/1
|
||
[AR1-GigabitEthernet0/0/1]ip add 192.168.1.254 24
|
||
[AR1-GigabitEthernet0/0/1]int g0/0/2
|
||
[AR1-GigabitEthernet0/0/2]ip add 192.168.2.254 24
|
||
```
|
||
|
||
### 二、ACL
|
||
|
||
- **AR1**
|
||
|
||
```
|
||
[AR1]acl 2000
|
||
[AR1-acl-basic-2000]rule 10 permit source 192.168.1.1 0.0.0.0
|
||
[AR1-acl-basic-2000]rule 20 deny source 192.168.1.0 0.0.0.255
|
||
[AR1-acl-basic-2000]quit
|
||
[AR1]int g0/0/0
|
||
[AR1-GigabitEthernet0/0/0]traffic-filter outbound acl 2000
|
||
```
|
||
|
||
***注释:***
|
||
|
||
1. `[AR1]acl 2000`:在设备AR1上创建一个编号为2000的基本ACL。
|
||
2. `[AR1-acl-basic-2000]rule 10 permit source 192.168.1.1 0.0.0.0`:在ACL 2000中添加规则10,该规则允许源IP地址为192.168.1.1的数据包通过。
|
||
3. `[AR1-acl-basic-2000]rule 20 deny source 192.168.1.0 0.0.0.255`:在ACL 2000中添加规则20,该规则拒绝源IP地址在192.168.1.0/24网段的数据包通过。
|
||
4. `[AR1-acl-basic-2000]quit`:退出ACL 2000的配置模式。
|
||
5. `[AR1]int g0/0/0`:进入设备AR1的GigabitEthernet0/0/0接口配置模式。
|
||
6. `[AR1-GigabitEthernet0/0/0]traffic-filter outbound acl 2000`:在GigabitEthernet0/0/0接口的出方向应用ACL 2000,以过滤出站流量。
|
||
|
||
> 需要注意的是,ACL规则的执行顺序是从上到下的,因此规则10和规则20的顺序很重要。在这个例子中,由于规则10先于规则20,所以只有源IP地址为192.168.1.1的数据包会被允许通过,而192.168.1.0/24网段的其他数据包将被拒绝。然而,由于规则20覆盖了规则10中的IP地址,实际上所有来自192.168.1.0/24网段的数据包都将被拒绝。这可能是配置错误,通常应该先配置拒绝规则,然后配置允许规则。
|
||
|
||
### 三、测试
|
||
|
||
- **PC间连通性测试**
|
||
|
||
> 全通
|
||
|
||
- **PC PING Server**
|
||
|
||
- PC1
|
||
|
||
```
|
||
PC>ping 192.168.3.1
|
||
|
||
Ping 192.168.3.1: 32 data bytes, Press Ctrl_C to break
|
||
Request timeout!
|
||
From 192.168.3.1: bytes=32 seq=2 ttl=254 time=31 ms
|
||
From 192.168.3.1: bytes=32 seq=3 ttl=254 time=32 ms
|
||
From 192.168.3.1: bytes=32 seq=4 ttl=254 time=31 ms
|
||
From 192.168.3.1: bytes=32 seq=5 ttl=254 time=31 ms
|
||
|
||
--- 192.168.3.1 ping statistics ---
|
||
5 packet(s) transmitted
|
||
4 packet(s) received
|
||
20.00% packet loss
|
||
round-trip min/avg/max = 0/31/32 ms
|
||
```
|
||
|
||
- PC2
|
||
|
||
```
|
||
PC>ping 192.168.3.1
|
||
|
||
Ping 192.168.3.1: 32 data bytes, Press Ctrl_C to break
|
||
Request timeout!
|
||
Request timeout!
|
||
Request timeout!
|
||
Request timeout!
|
||
Request timeout!
|
||
|
||
--- 192.168.3.1 ping statistics ---
|
||
5 packet(s) transmitted
|
||
0 packet(s) received
|
||
100.00% packet loss
|
||
```
|
||
|
||
- PC3
|
||
|
||
```
|
||
PC>ping 192.168.3.1
|
||
|
||
Ping 192.168.3.1: 32 data bytes, Press Ctrl_C to break
|
||
From 192.168.3.1: bytes=32 seq=1 ttl=254 time=16 ms
|
||
From 192.168.3.1: bytes=32 seq=2 ttl=254 time=15 ms
|
||
From 192.168.3.1: bytes=32 seq=3 ttl=254 time=16 ms
|
||
From 192.168.3.1: bytes=32 seq=4 ttl=254 time<1 ms
|
||
From 192.168.3.1: bytes=32 seq=5 ttl=254 time=16 ms
|
||
|
||
--- 192.168.3.1 ping statistics ---
|
||
5 packet(s) transmitted
|
||
5 packet(s) received
|
||
0.00% packet loss
|
||
round-trip min/avg/max = 0/12/16 ms
|
||
```
|
||
|
||
|