131 lines
3.7 KiB
Markdown
131 lines
3.7 KiB
Markdown
# ACL
|
||
|
||
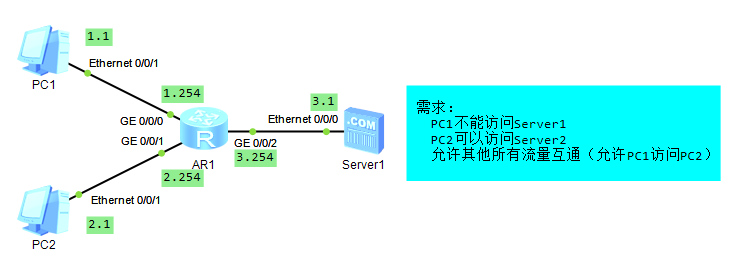
|
||
|
||
### 一、IP
|
||
|
||
- **PC & Server**
|
||
|
||
- **AR1**
|
||
|
||
```
|
||
[AR1]int g0/0/0
|
||
[AR1-GigabitEthernet0/0/0]ip add 192.168.1.254 24
|
||
[AR1-GigabitEthernet0/0/0]int g0/0/1
|
||
[AR1-GigabitEthernet0/0/1]ip add 192.168.2.254 24
|
||
[AR1-GigabitEthernet0/0/1]int g0/0/2
|
||
[AR1-GigabitEthernet0/0/2]ip add 192.168.3.254 24
|
||
```
|
||
|
||
### 二、ACL
|
||
|
||
- **AR1**
|
||
|
||
```
|
||
[AR1]acl 2000
|
||
[AR1-acl-basic-2000]rule 10 deny source 192.168.1.1 0.0.0.0
|
||
[AR1-acl-basic-2000]quit
|
||
[AR1]int g0/0/2
|
||
[AR1-GigabitEthernet0/0/0]traffic-filter outbound acl 2000
|
||
```
|
||
|
||
*解释:*
|
||
|
||
- `[AR1]acl 2000`:这个命令创建了一个编号为2000的基本ACL。在华为设备上,基本ACL的编号范围是2000-2999。
|
||
|
||
- `[AR1-acl-basic-2000]rule 10 deny source 192.168.1.1 0.0.0.0`:这个命令在ACL 2000中添加了一条规则,规则编号为10。这条规则的作用是拒绝源IP地址为192.168.1.1的所有流量。`0.0.0.0`表示一个通配符掩码,这里它被用来指定一个精确的IP地址匹配,因为0.0.0.0表示所有比特位都必须匹配。
|
||
|
||
具体来说,这条ACL规则做了以下事情:
|
||
|
||
- `rule 10`:定义了规则的编号,规则编号决定了规则的执行顺序,编号越小,优先级越高。
|
||
- `deny`:表示动作是拒绝匹配规则的流量。
|
||
- `source 192.168.1.1 0.0.0.0`:定义了匹配条件,即源IP地址必须精确为192.168.1.1。
|
||
|
||
- `[AR1-GigabitEthernet0/0/0]traffic-filter outbound acl 2000`:在g0/0/0接口上应用ACL 2000,以过滤出站流量。
|
||
|
||
|
||
|
||

|
||
|
||
### 三、测试
|
||
|
||
- **PC1**
|
||
|
||
- PING PC2
|
||
|
||
```
|
||
PC>ping 192.168.2.1
|
||
|
||
Ping 192.168.2.1: 32 data bytes, Press Ctrl_C to break
|
||
Request timeout!
|
||
From 192.168.2.1: bytes=32 seq=2 ttl=127 time<1 ms
|
||
From 192.168.2.1: bytes=32 seq=3 ttl=127 time=15 ms
|
||
From 192.168.2.1: bytes=32 seq=4 ttl=127 time=16 ms
|
||
From 192.168.2.1: bytes=32 seq=5 ttl=127 time=15 ms
|
||
|
||
--- 192.168.2.1 ping statistics ---
|
||
5 packet(s) transmitted
|
||
4 packet(s) received
|
||
20.00% packet loss
|
||
round-trip min/avg/max = 0/11/16 ms
|
||
```
|
||
|
||
- PING Server
|
||
|
||
```
|
||
PC>ping 192.168.3.1
|
||
|
||
Ping 192.168.3.1: 32 data bytes, Press Ctrl_C to break
|
||
Request timeout!
|
||
Request timeout!
|
||
Request timeout!
|
||
Request timeout!
|
||
Request timeout!
|
||
|
||
--- 192.168.3.1 ping statistics ---
|
||
5 packet(s) transmitted
|
||
0 packet(s) received
|
||
100.00% packet loss
|
||
```
|
||
|
||
- **PC2**
|
||
|
||
- PING PC1
|
||
|
||
```
|
||
PC>ping 192.168.1.1
|
||
|
||
Ping 192.168.1.1: 32 data bytes, Press Ctrl_C to break
|
||
From 192.168.1.1: bytes=32 seq=1 ttl=127 time=16 ms
|
||
From 192.168.1.1: bytes=32 seq=2 ttl=127 time=16 ms
|
||
From 192.168.1.1: bytes=32 seq=3 ttl=127 time=15 ms
|
||
From 192.168.1.1: bytes=32 seq=4 ttl=127 time<1 ms
|
||
From 192.168.1.1: bytes=32 seq=5 ttl=127 time<1 ms
|
||
|
||
--- 192.168.1.1 ping statistics ---
|
||
5 packet(s) transmitted
|
||
5 packet(s) received
|
||
0.00% packet loss
|
||
round-trip min/avg/max = 0/9/16 ms
|
||
```
|
||
|
||
- PING Server
|
||
|
||
```
|
||
PC>ping 192.168.3.1
|
||
|
||
Ping 192.168.3.1: 32 data bytes, Press Ctrl_C to break
|
||
From 192.168.3.1: bytes=32 seq=1 ttl=254 time=16 ms
|
||
From 192.168.3.1: bytes=32 seq=2 ttl=254 time=15 ms
|
||
From 192.168.3.1: bytes=32 seq=3 ttl=254 time=16 ms
|
||
From 192.168.3.1: bytes=32 seq=4 ttl=254 time<1 ms
|
||
From 192.168.3.1: bytes=32 seq=5 ttl=254 time=16 ms
|
||
|
||
--- 192.168.3.1 ping statistics ---
|
||
5 packet(s) transmitted
|
||
5 packet(s) received
|
||
0.00% packet loss
|
||
round-trip min/avg/max = 0/12/16 ms
|
||
```
|
||
|
||
|