2024年10月4日 14:08:24
This commit is contained in:
parent
9f68c700aa
commit
081920d4b4
@ -184,7 +184,7 @@
|
||||
|
||||
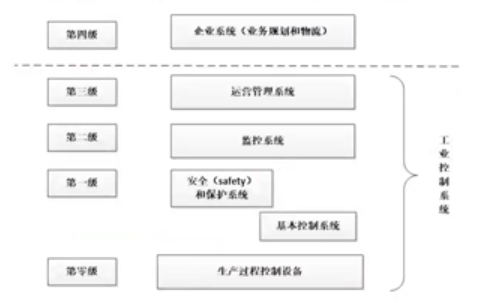
#### 2、工业控制系统体系结构
|
||||
|
||||
|
||||

|
||||
|
||||
#### 3、工业控制系统安全威胁
|
||||
|
||||
@ -245,7 +245,7 @@
|
||||
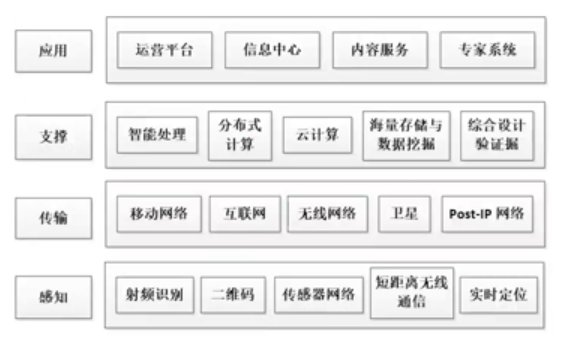
| 感知 | 传输 | 支撑 | 应用 |
|
||||
| ---- | ---- | ---- | ---- |
|
||||
|
||||
|
||||

|
||||
|
||||
1. **感知层安全**
|
||||
- 网关节点被控制,拒绝服务
|
||||
|
||||
@ -63,7 +63,7 @@
|
||||
|
||||
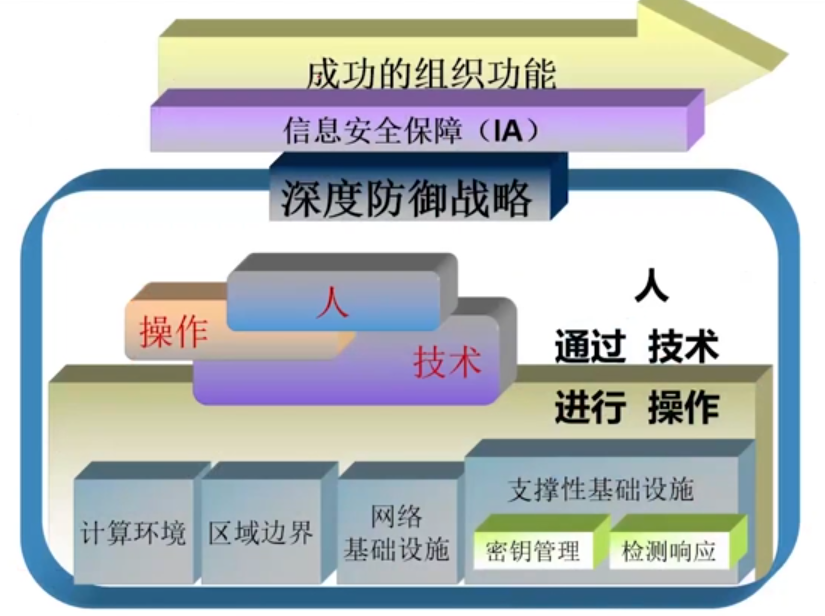
"深度防御(纵深防御)"
|
||||
|
||||
|
||||

|
||||
|
||||
#### 3、三个要素
|
||||
|
||||
@ -156,13 +156,13 @@
|
||||
|
||||
- P33 图1-7
|
||||
|
||||
|
||||

|
||||
|
||||
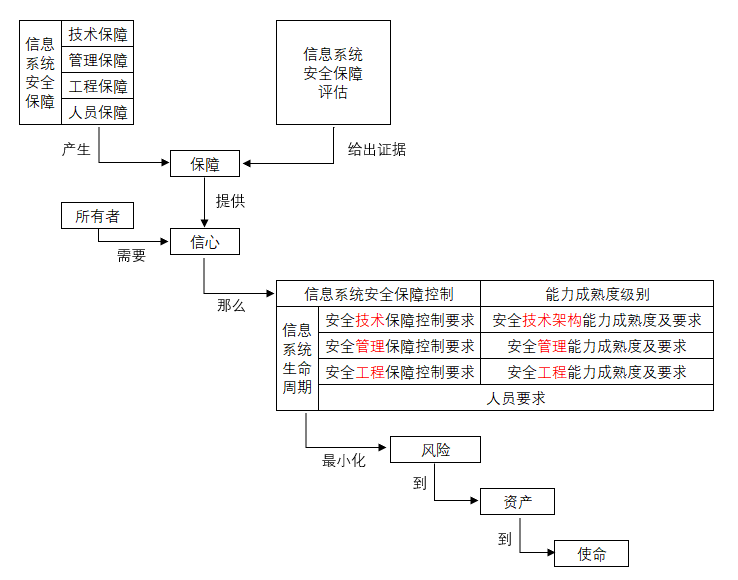
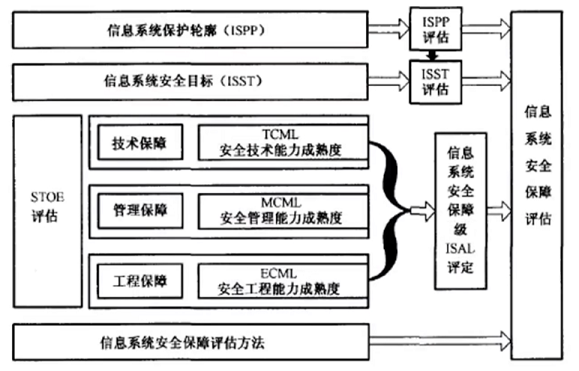
- **信息系统安全保障评估描述**
|
||||
|
||||
- P34 图1-8
|
||||
|
||||
|
||||

|
||||
|
||||
- <span style="background-color:yellow;">信息系统保护轮廓(ISPP)</span>
|
||||
|
||||
@ -180,7 +180,7 @@
|
||||
|
||||
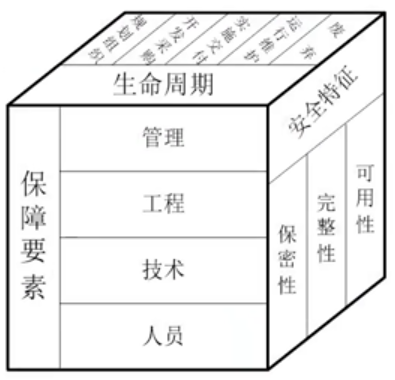
- P35 图1.9
|
||||
|
||||
|
||||

|
||||
|
||||
- 模型特点
|
||||
|
||||
@ -195,7 +195,7 @@
|
||||
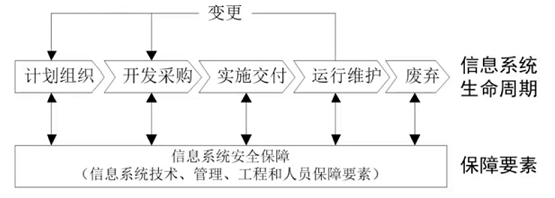
- 信息系统的生命周期层面和保障要素层面不是相互孤立的,而是<span style="background-color:yellow;">相互关联</span>、<span style="background-color:yellow;">密不可分</span>的。
|
||||
- 在信息系统生命周期中的任何时间点上,都需要综合信息系统安全保障的技术、管理、工程和人员保障要素。
|
||||
|
||||
|
||||

|
||||
|
||||
- **信息安全保障要素**
|
||||
|
||||
@ -240,7 +240,7 @@
|
||||
|
||||
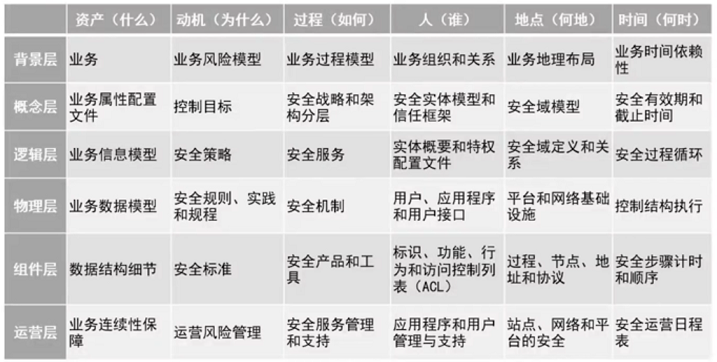
- <span style="color:red;">分层</span>的模型,包括<span style="color:red;">六个</span>层级
|
||||
|
||||
|
||||

|
||||
|
||||
- 背景层(业务视图)
|
||||
|
||||
|
||||
@ -41,7 +41,7 @@
|
||||
|
||||
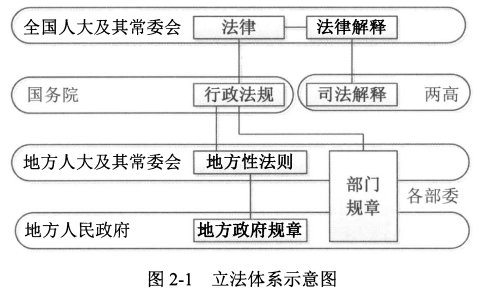
#### 2、我国采取<span style="color:red;">多级立法</span>机制
|
||||
|
||||
|
||||

|
||||
|
||||
#### 3、对传统的网络安全制度进行立法修正
|
||||
|
||||
@ -62,7 +62,7 @@
|
||||
|
||||
《网络安全法》从草案发布到正式出台,共经历了<span style="background-color:yellow;">三次审议</span>,<span style="background-color:yellow;">两次公开征求意见和修改</span>。
|
||||
|
||||

|
||||

|
||||
|
||||
#### 2、基本概念
|
||||
|
||||
@ -86,7 +86,7 @@
|
||||
|
||||
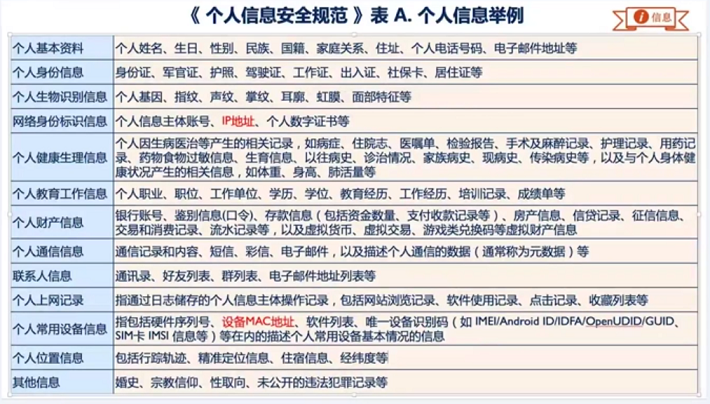
> 个人信息是指以电子或者其他方式记录的能够单独或者与其他信息结果识别自然人个人身份的各种信息,包括但不限于自然人的姓名、出生日期、身份证件号码、个人生物识别信息、住址、电话号码等。
|
||||
|
||||
|
||||

|
||||
|
||||
- **网络数据**
|
||||
|
||||
@ -98,7 +98,7 @@
|
||||
|
||||
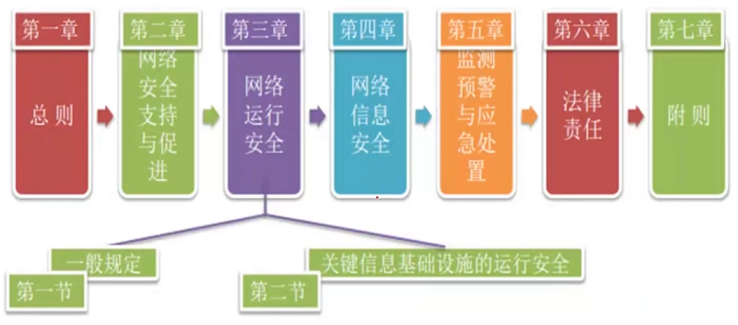
**<span style="color:red;">七章 79条</span>**
|
||||
|
||||
|
||||

|
||||
|
||||
- **第一章 总则**
|
||||
|
||||
@ -106,7 +106,7 @@
|
||||
|
||||
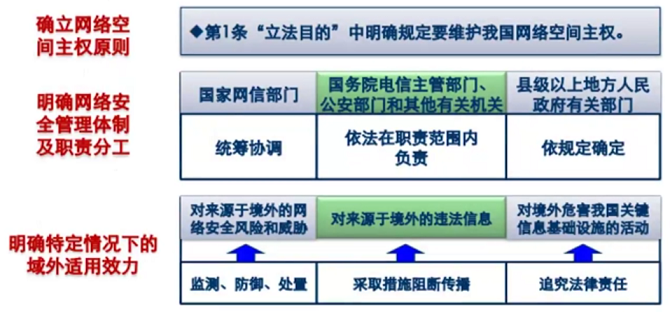
作为我国网络安全治理的基本法,《网络安全法》在总则部分确立了网络<span style="color:red;">主权原则</span>,明确了网络安全管理体制和分工,及域外的适用效力。
|
||||
|
||||
|
||||

|
||||
|
||||
- **第二章 网络安全支持与促进**
|
||||
|
||||
@ -220,15 +220,15 @@
|
||||
|
||||
- *重视对个人信息保护*
|
||||
|
||||
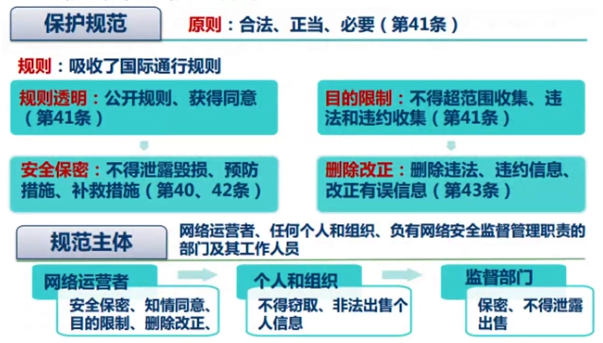
|
||||

|
||||
|
||||
- *规范信息管理*
|
||||
|
||||
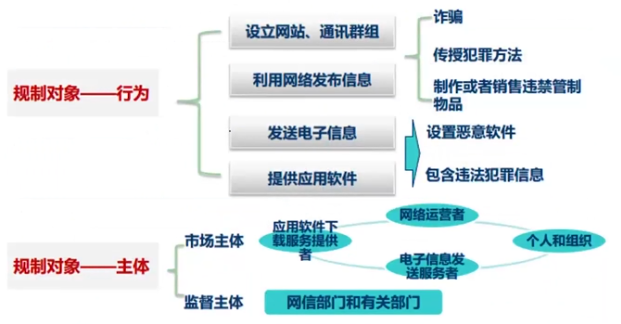
|
||||

|
||||
|
||||
- *确定信息管理中相关职责*
|
||||
|
||||
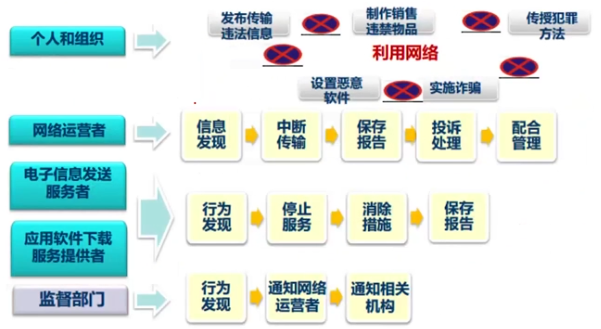
|
||||

|
||||
|
||||
- 2017年05月02日国家互联网信息办公室正式发布<span style="color:red;">《互联网新闻信息服务管理规定》(国信办1号令)</span>,于6月1日同《网络安全法》一起实施。
|
||||
|
||||
@ -244,13 +244,13 @@
|
||||
|
||||
- *工作制度化、法治化*
|
||||
|
||||
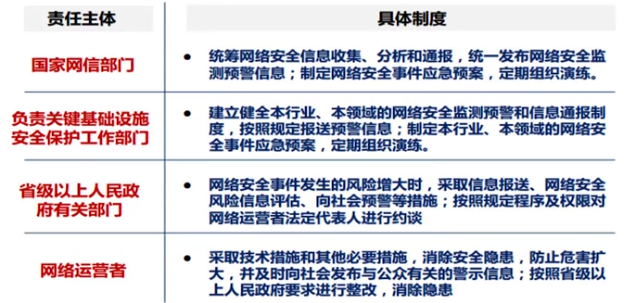
|
||||

|
||||
|
||||
- **第六章 法律责任**
|
||||
|
||||
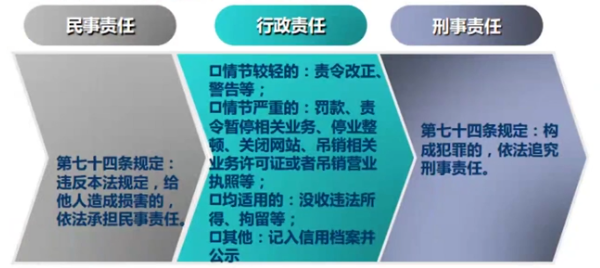
- 对违反《网络安全法》的行为,第六章规定了<span style="color:red;">民事责任、行政责任、刑事责任</span>
|
||||
|
||||
|
||||

|
||||
|
||||
### 四、网络安全相关法规
|
||||
|
||||
|
||||
@ -70,7 +70,7 @@
|
||||
|
||||
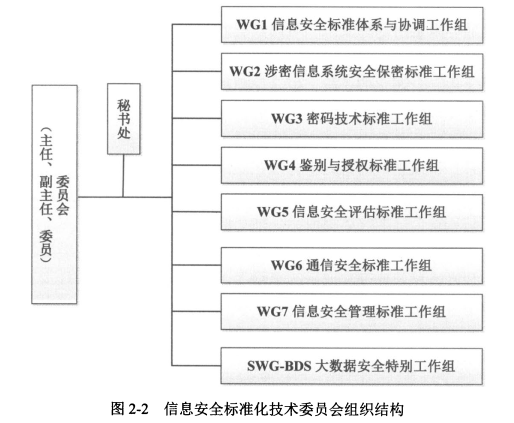
- **TC260组织结构**
|
||||
|
||||
|
||||

|
||||
|
||||
- **我国标准分类**
|
||||
|
||||
@ -86,7 +86,7 @@
|
||||
|
||||
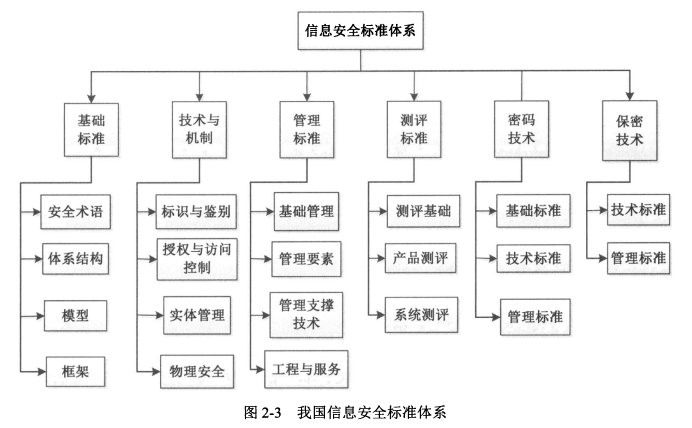
#### 1、信息安全标准体系
|
||||
|
||||
|
||||

|
||||
|
||||
#### 2、基础类标准
|
||||
|
||||
@ -129,7 +129,7 @@
|
||||
|
||||
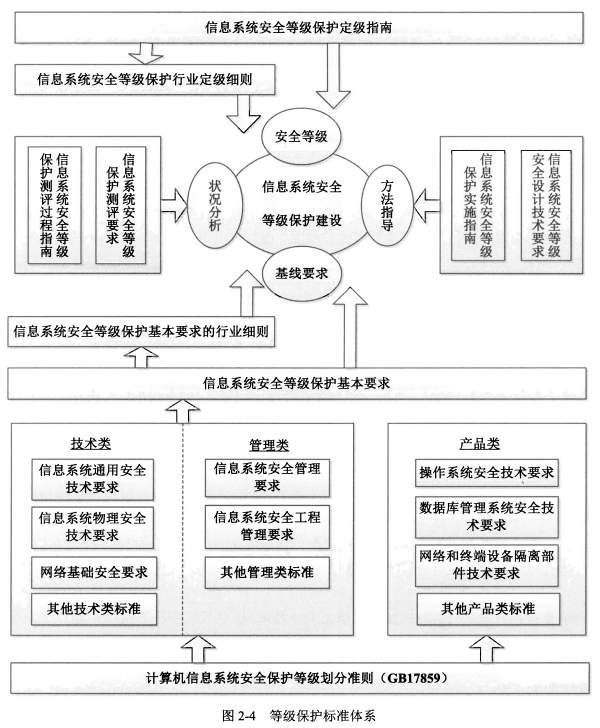
#### 1、信息系统安全等级保护定级指南
|
||||
|
||||
|
||||

|
||||
|
||||
- **<span style="color:red;">安全等级类</span>**:主要对<span style="color:red;">如何进行信息系统定级</span>做出指导
|
||||
|
||||
@ -180,11 +180,11 @@
|
||||
|
||||
#### 2、等级保护定级方法(V2.0)
|
||||
|
||||

|
||||

|
||||
|
||||
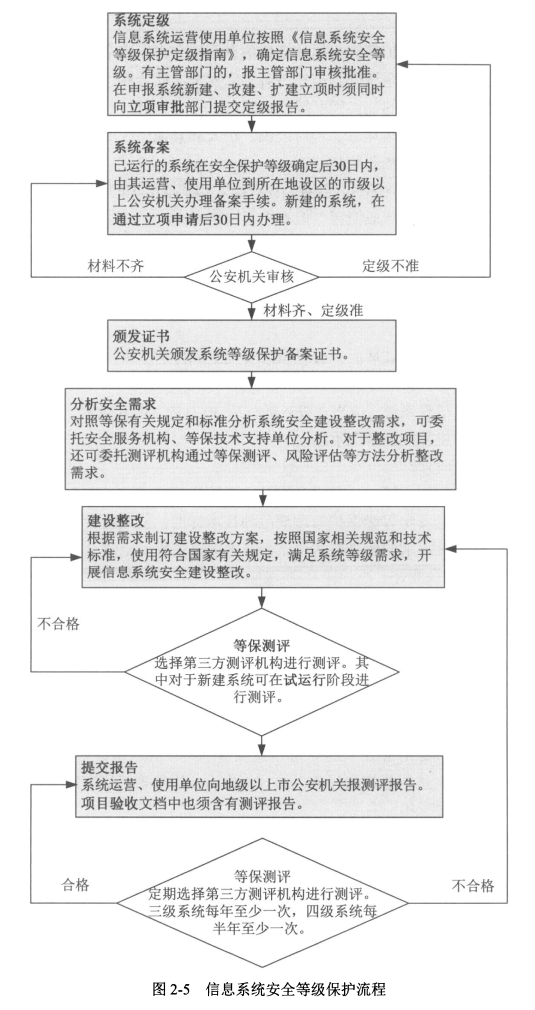
#### 3、等级保护工作流程
|
||||
|
||||
|
||||

|
||||
|
||||
- **等级保护阶段**
|
||||
- GB/T 25058—2010
|
||||
@ -213,7 +213,7 @@
|
||||
|
||||
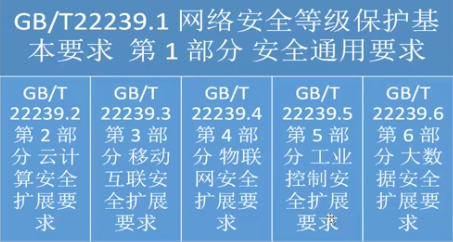
#### 4、等级保护要求体系 - <span style="color:red;">等保2.0</span>
|
||||
|
||||
|
||||

|
||||
|
||||
- **等级保护扩展要求**
|
||||
- 云计算安全要求
|
||||
|
||||
@ -54,7 +54,7 @@
|
||||
- 信息安全管理是信息安全技术的融合剂,保障各项技术措施能够发挥作用
|
||||
- 信息安全管理能<span style="color:red;">预防</span>、<span style="color:red;">阻止</span>或<span style="color:red;">减少</span>信息安全事件的发生
|
||||
|
||||
|
||||

|
||||
|
||||
#### 2、对组织的价值
|
||||
|
||||
|
||||
@ -57,7 +57,7 @@
|
||||
|
||||
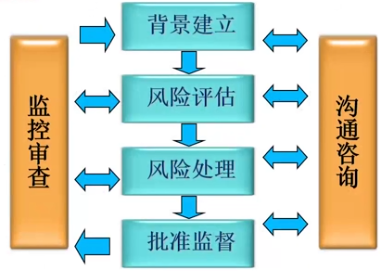
**<span style="color:red;">四个阶段 </span>&& <span style="color:red;">两个贯穿</span>**
|
||||
|
||||
|
||||

|
||||
|
||||
#### <span style="background-color:cyan;">2、四个阶段</span>
|
||||
|
||||
@ -141,4 +141,3 @@
|
||||
1. 向上沟通:要共识
|
||||
2. 向下沟通:要落实
|
||||
3. 水平沟通:要支持 / 协调
|
||||
|
||||
|
||||
@ -20,7 +20,7 @@
|
||||
|
||||
组织在<span style="color:red;">整体</span>或<span style="color:red;">特定范围</span>内建立的信息安全方针和目标,以及为完成这些目标所用的方法和体系。它是直接管理活动的结果,表示为<span style="background-color:yellow;">方针、原则、目标方法、计划、活动、程序、过程和资源</span>的<span style="color:red;">集合</span>。
|
||||
|
||||
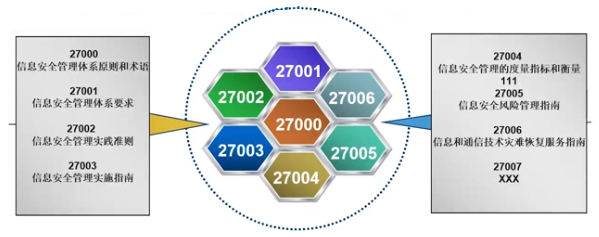
|
||||

|
||||
|
||||
#### 2、信息安全管理体系建设<span style="color:red;">成功的因素</span>
|
||||
|
||||
@ -53,15 +53,15 @@
|
||||
|
||||
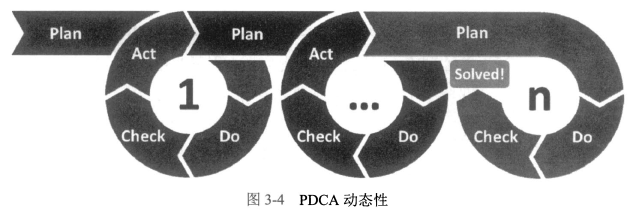
- PDCA 动态性
|
||||
|
||||
|
||||

|
||||
|
||||
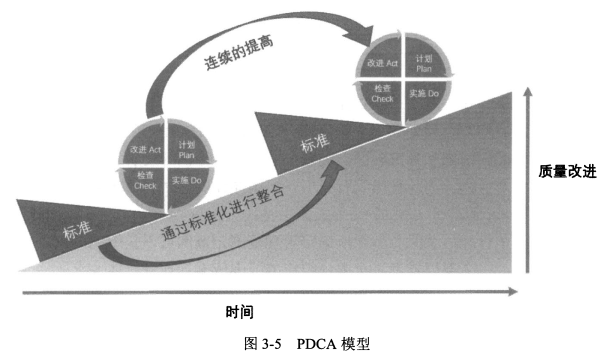
- PDCA 模型
|
||||
|
||||
|
||||

|
||||
|
||||
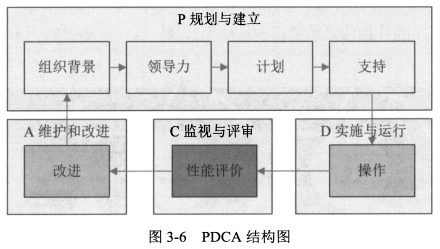
- <span style="background-color:yellow;">PDCA 结构图</span>
|
||||
|
||||
|
||||

|
||||
|
||||
### 三、信息安全管理体系建设过程
|
||||
|
||||
@ -104,7 +104,7 @@
|
||||
|
||||
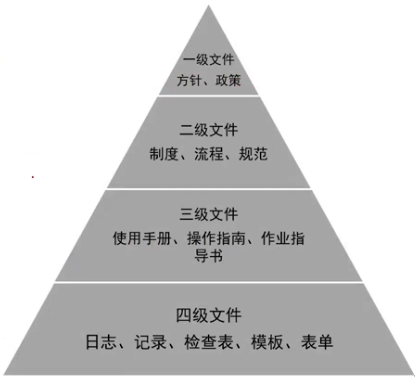
#### <span style="background-color:yellow;">1、文档结构(考点)</span>
|
||||
|
||||
|
||||

|
||||
|
||||
| 一级文件<span style="color:red;">定目标</span> | 二级文件<span style="color:red;">定措施</span> | 三级文件<span style="color:red;">看执行</span> | 四级文件<span style="color:red;">看结果</span> |
|
||||
| ---------------------------------------------- | ---------------------------------------------- | ---------------------------------------------- | ---------------------------------------------- |
|
||||
|
||||
@ -30,9 +30,9 @@
|
||||
- 35个目标
|
||||
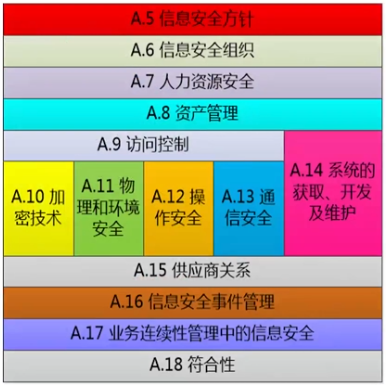
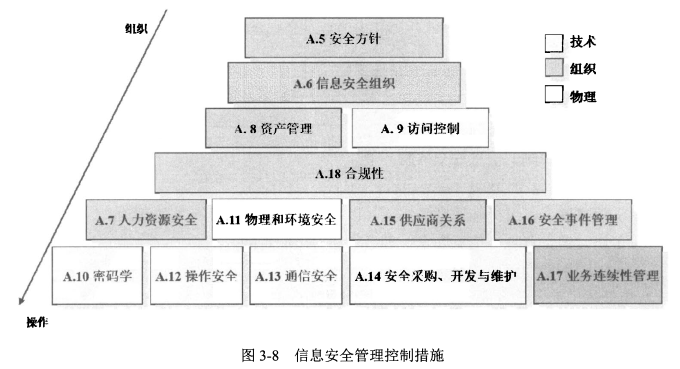
- 114个控制措施
|
||||
|
||||
|
||||

|
||||
|
||||
|
||||

|
||||
|
||||
#### 2、描述方式(ISO 27002)
|
||||
|
||||
@ -63,7 +63,7 @@
|
||||
|
||||
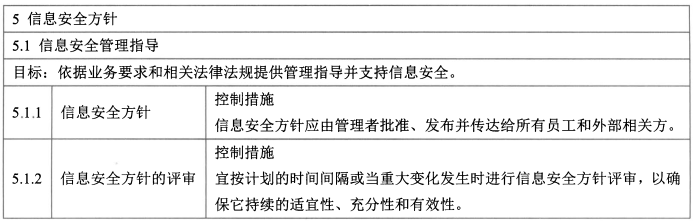
宜按<span style="color:red;">计划的时间间隔(通常1年)</span>或<span style="color:red;">当重大变化发生时</span>进行信息安全方针<span style="color:red;">评审</span>,以确保它持续的<span style="color:red;">适宜性</span>、<span style="color:red;">充分性</span>和<span style="color:red;">有效性</span>。
|
||||
|
||||
|
||||

|
||||
|
||||
#### 2、信息安全组织(2/7)
|
||||
|
||||
@ -76,7 +76,7 @@
|
||||
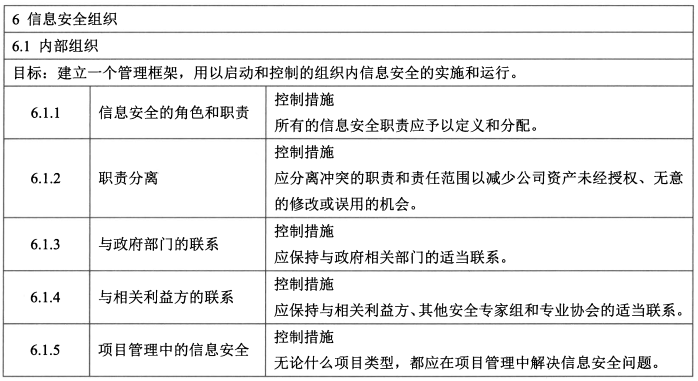
- 信息安全角色:CEO、CIO、CFO、CISO/CSO、SA(Adminsitrator)、SA(Auditor)、SafeGuard(安保人员)
|
||||
- <span style="background-color:yellow;">职责分离</span>
|
||||
|
||||
|
||||

|
||||
|
||||
- **移动设备与远程办公 - 2**
|
||||
|
||||
@ -87,7 +87,7 @@
|
||||
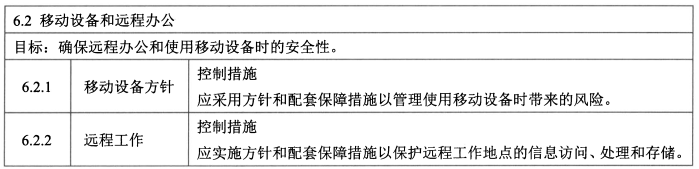
- 移动设备方针,管理移动带来的风险
|
||||
- 保护远程工作地点的信息访问、处理和存储
|
||||
|
||||
|
||||

|
||||
|
||||
#### 3、人力资源安全(3/6)
|
||||
|
||||
@ -97,7 +97,7 @@
|
||||
|
||||
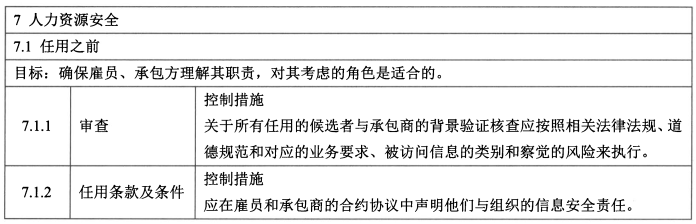
- 控制措施:审查、任用条款及条件
|
||||
|
||||
|
||||

|
||||
|
||||
- **<span style="background-color:yellow;">任用中 - 3</span>**
|
||||
|
||||
@ -105,7 +105,7 @@
|
||||
|
||||
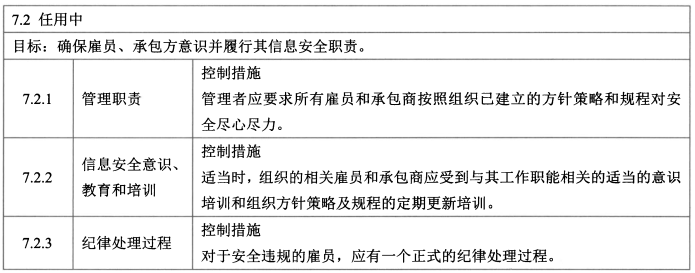
- 控制措施:管理职责、意识教育和培训、纪律处理
|
||||
|
||||
|
||||

|
||||
|
||||
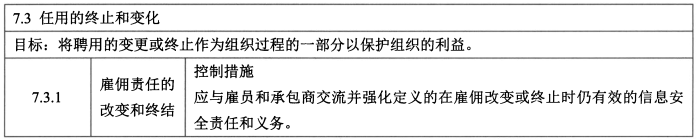
- **<span style="background-color:yellow;">任用终止和变化 - 1</span>**
|
||||
|
||||
@ -113,7 +113,7 @@
|
||||
|
||||
- 控制措施:雇佣责任的改变和终结
|
||||
|
||||
|
||||

|
||||
|
||||
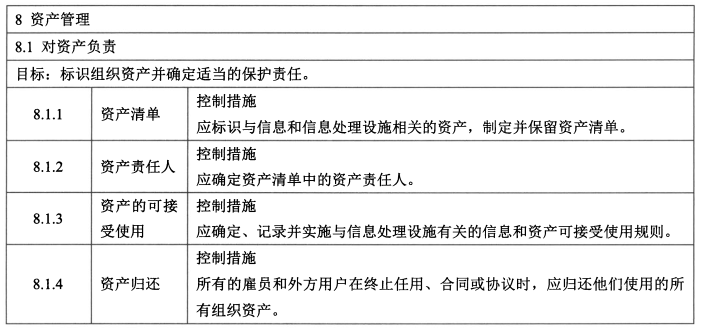
#### 4、资产管理(3/10)
|
||||
|
||||
@ -123,7 +123,7 @@
|
||||
|
||||
- 控制措施:资产清单、资产责任人、资产的可接受使用、资产归还
|
||||
|
||||
|
||||

|
||||
|
||||
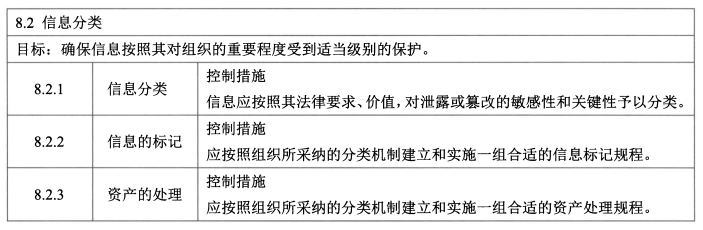
- **<span style="background-color:yellow;">信息分类 - 3</span>**
|
||||
|
||||
@ -131,7 +131,7 @@
|
||||
|
||||
- 控制措施:分类指南、信息的标记、资产的处理
|
||||
|
||||
|
||||

|
||||
|
||||
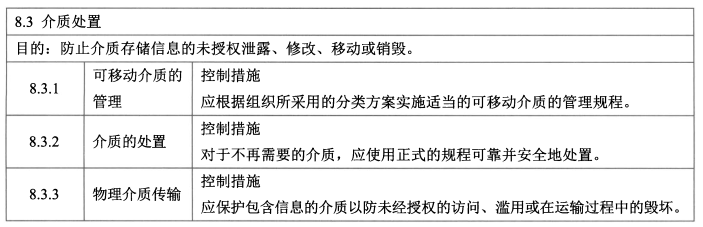
- **介质处理 - 3**
|
||||
|
||||
@ -139,7 +139,7 @@
|
||||
|
||||
- 控制措施:可移动介质的管理、介质的处置、物理介质传输
|
||||
|
||||
|
||||

|
||||
|
||||
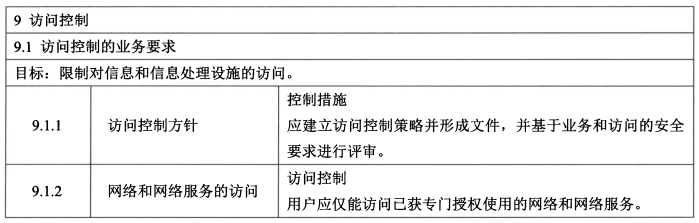
#### 5、访问控制(4/14)
|
||||
|
||||
@ -149,7 +149,7 @@
|
||||
|
||||
- 控制措施:访问控制方针、网络和网络服务的访问
|
||||
|
||||
|
||||

|
||||
|
||||
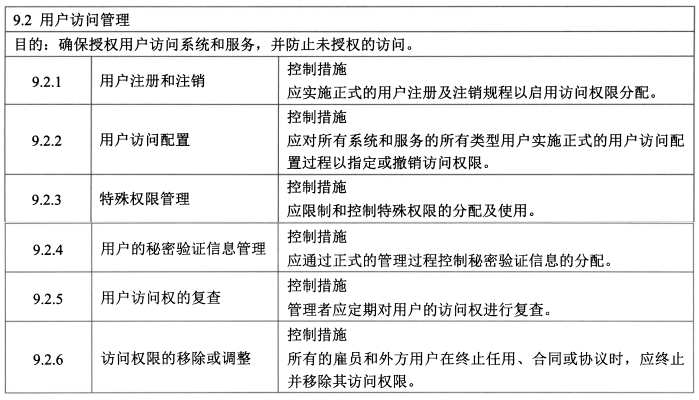
- **用户访问管理 - 6**
|
||||
|
||||
@ -157,7 +157,7 @@
|
||||
|
||||
- 控制措施:用户注册和注销、用户访问配置、特殊权限管理、用户的秘密验证信息管理、用户访问权的复查、访问权限的移除或调整
|
||||
|
||||
|
||||

|
||||
|
||||
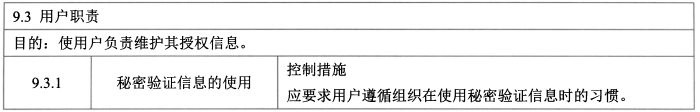
- **用户职责 - 1**
|
||||
|
||||
@ -165,7 +165,7 @@
|
||||
|
||||
- 控制措施:秘密验证信息的使用
|
||||
|
||||
|
||||

|
||||
|
||||
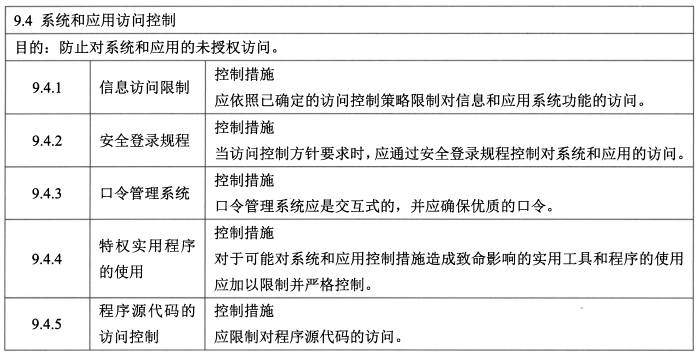
- **系统和应用访问控制 - 5**
|
||||
|
||||
@ -173,7 +173,7 @@
|
||||
|
||||
- 控制措施:信息访问限制、安全登录规程、口令管理系统、特权实用程序的使用、程序源代码的访问控制
|
||||
|
||||
|
||||

|
||||
|
||||
#### 6、密码学(1/2)
|
||||
|
||||
@ -186,7 +186,7 @@
|
||||
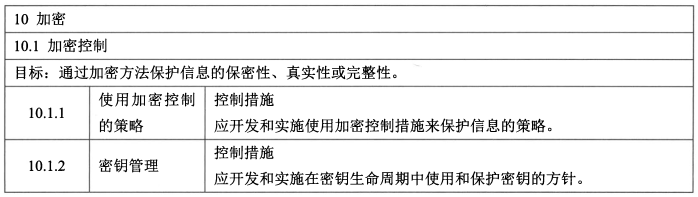
- 使用加密控制的策略
|
||||
- 密钥管理
|
||||
|
||||
|
||||

|
||||
|
||||
#### 7、物理与环境安全(2/15)
|
||||
|
||||
@ -196,7 +196,7 @@
|
||||
|
||||
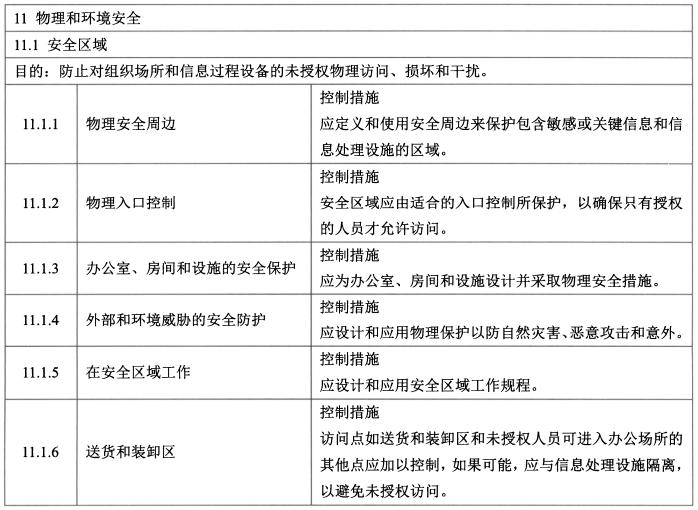
- 控制措施:物理安全边界、物理入口控制、<span style="color:blue;">办公室</span>、<span style="color:blue;">房间和设施的安全保护</span>、外部和环境威胁的安全防护、<span style="color:blue;">在安全区域工作</span>、<span style="color:blue;">送货和装卸区</span>。
|
||||
|
||||
|
||||

|
||||
|
||||
- **设备安全 - 9**
|
||||
|
||||
@ -204,7 +204,7 @@
|
||||
|
||||
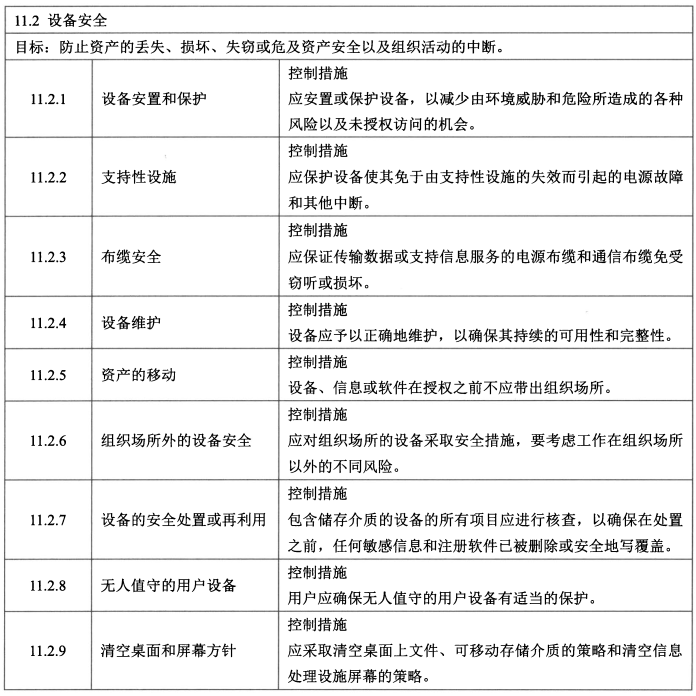
- 控制措施:设备安置和保护、支持性设施、布缆安全、设备维护、资产的移动、组织场所外的设备安全、设备的安全处置和再利用、无人值守的用户设备清空桌面和屏幕方针。
|
||||
|
||||
|
||||

|
||||
|
||||
#### 8、操作安全(7/14)
|
||||
|
||||
@ -214,7 +214,7 @@
|
||||
|
||||
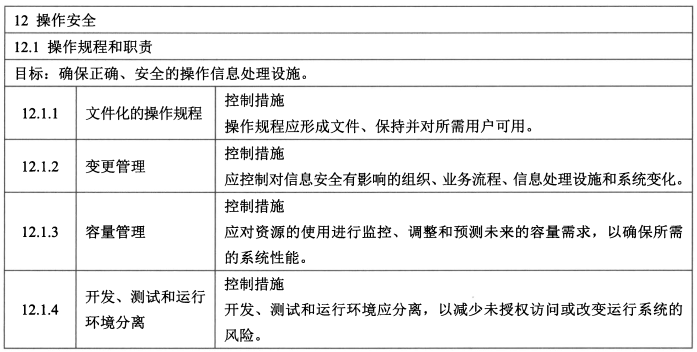
- 控制措施:文件化的操作规程、变更管理、容量管理、开发、测试和运行环境分离
|
||||
|
||||
|
||||

|
||||
|
||||
- **恶意代码防范 - 1**
|
||||
|
||||
@ -222,7 +222,7 @@
|
||||
|
||||
- 控制措施:控制恶意代码
|
||||
|
||||

|
||||

|
||||
|
||||
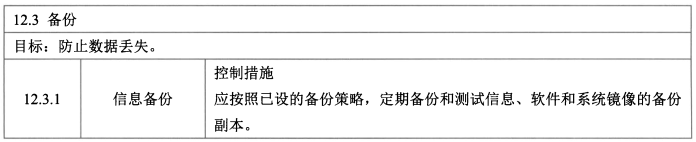
- **备份 - 1**
|
||||
|
||||
@ -230,7 +230,7 @@
|
||||
|
||||
- 控制措施:信息备份
|
||||
|
||||
|
||||

|
||||
|
||||
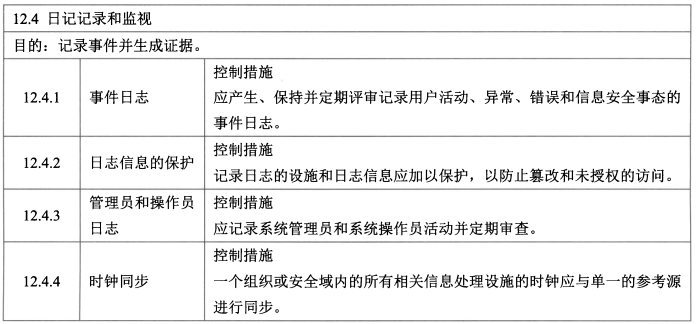
- **日志记录和监视 - 4**
|
||||
|
||||
@ -238,7 +238,7 @@
|
||||
|
||||
- 控制措施:事件日志、日志信息的保护、管理员和操作员日志、时钟同步
|
||||
|
||||
|
||||

|
||||
|
||||
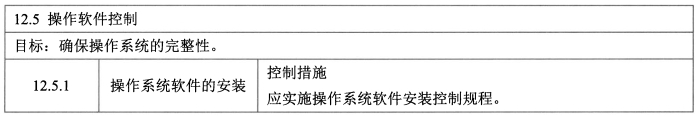
- **操作软件控制 - 1**
|
||||
|
||||
@ -246,7 +246,7 @@
|
||||
|
||||
- 控制措施:操作系统软件的安装
|
||||
|
||||
|
||||

|
||||
|
||||
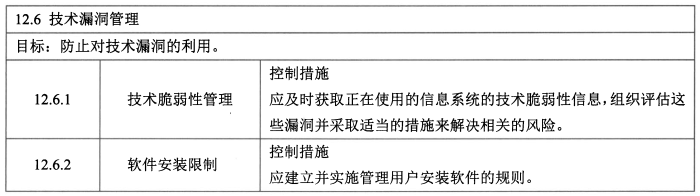
- **技术漏洞管理 - 2**
|
||||
|
||||
@ -254,7 +254,7 @@
|
||||
|
||||
- 控制措施:技术脆弱性管理、软件安装限制
|
||||
|
||||
|
||||

|
||||
|
||||
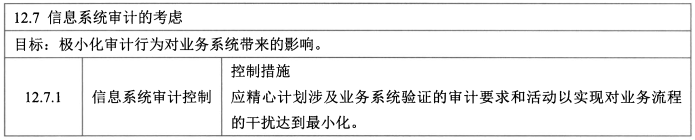
- **信息系统审计的考虑 - 1**
|
||||
|
||||
@ -262,7 +262,7 @@
|
||||
|
||||
- 控制措施:信息系统审计控制。
|
||||
|
||||
|
||||

|
||||
|
||||
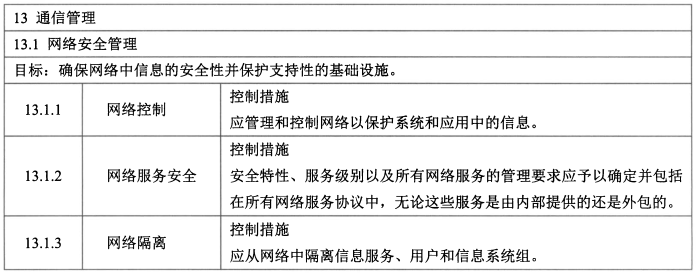
#### 9、通讯安全(2/7)
|
||||
|
||||
@ -272,7 +272,7 @@
|
||||
|
||||
- 控制措施:网络控制、网络服务安全、网络隔离。
|
||||
|
||||
|
||||

|
||||
|
||||
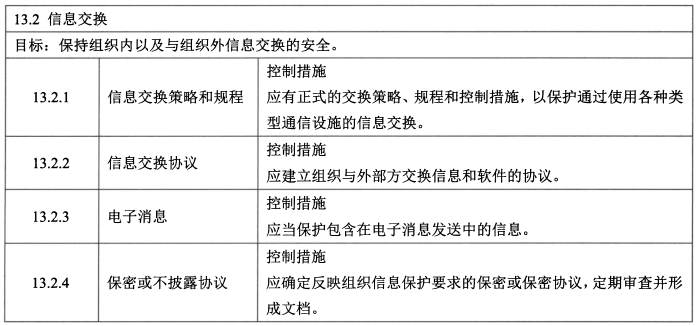
- **信息的交换 - 4**
|
||||
|
||||
@ -280,7 +280,7 @@
|
||||
|
||||
- 控制措施:信息交换策略和规程、信息交换协议、电子消息、保密或不披露协议。
|
||||
|
||||
|
||||

|
||||
|
||||
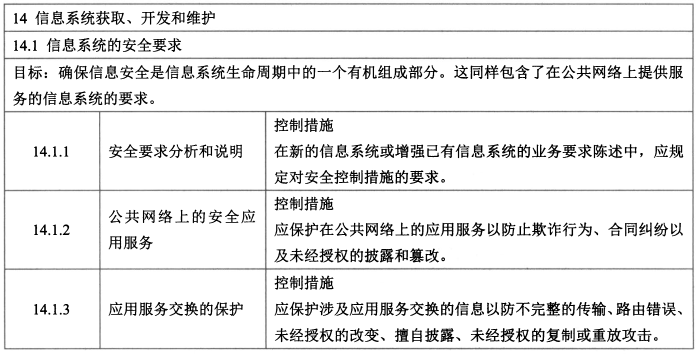
#### 10、信息的获取开发及维护(3/13)
|
||||
|
||||
@ -290,7 +290,7 @@
|
||||
|
||||
- 控制措施:安全需求分析和说明、公共网络上的安全应用服务、应用服务交换的保护。
|
||||
|
||||
|
||||

|
||||
|
||||
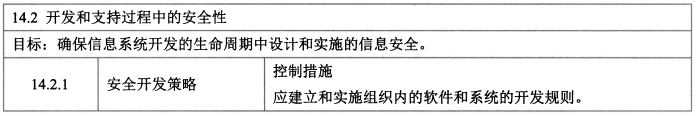
- **开发和支持过程中的安全 - 9**
|
||||
|
||||
@ -298,9 +298,9 @@
|
||||
|
||||
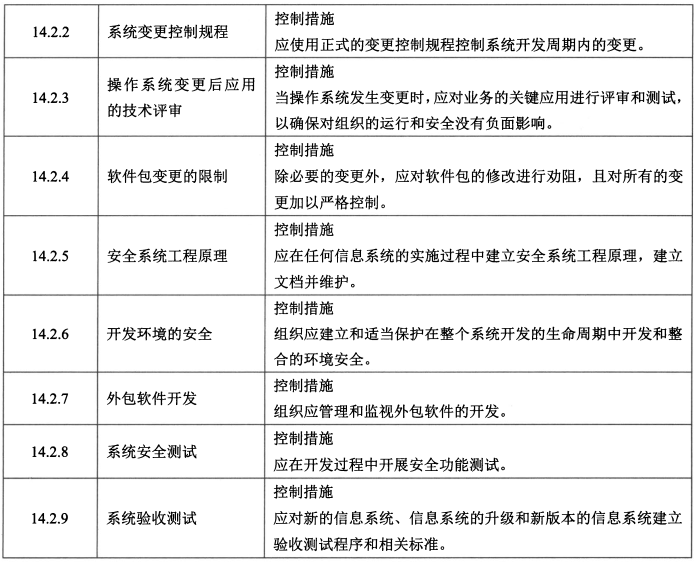
- 控制措施:安全开发策略、系统变更控制规程、操作系统变更后应用的技术评审、软件包变更的限制、安全系统工程原理、开发环境的安全、外包软件开发、系统安全测试、系统验收测试。
|
||||
|
||||
|
||||

|
||||
|
||||
|
||||

|
||||
|
||||
- **测试数据 - 1**
|
||||
|
||||
@ -308,7 +308,7 @@
|
||||
|
||||
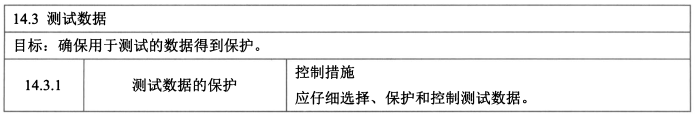
- 控制措施:测试数据的保护。
|
||||
|
||||
|
||||

|
||||
|
||||
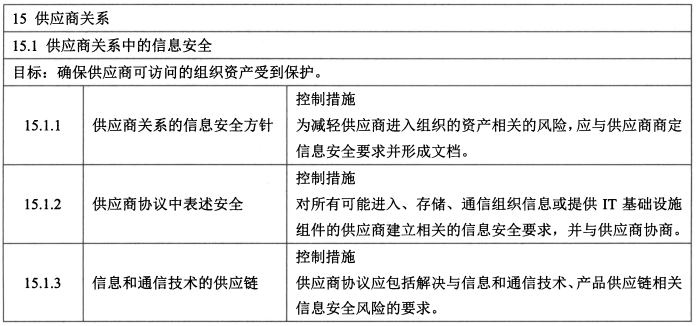
#### 11、供应商关系(2/5)
|
||||
|
||||
@ -318,7 +318,7 @@
|
||||
|
||||
- 控制措施:供应商关系的信息安全方针、供应商协议中解决安全问题、信息和通信技术的供应链。
|
||||
|
||||
|
||||

|
||||
|
||||
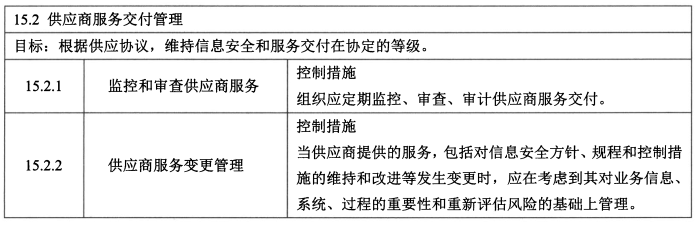
- **供应商服务交付管理 - 2**
|
||||
|
||||
@ -326,7 +326,7 @@
|
||||
|
||||
- 控制措施:监控和审查供应商服务、供应商服务变更管理。
|
||||
|
||||
|
||||

|
||||
|
||||
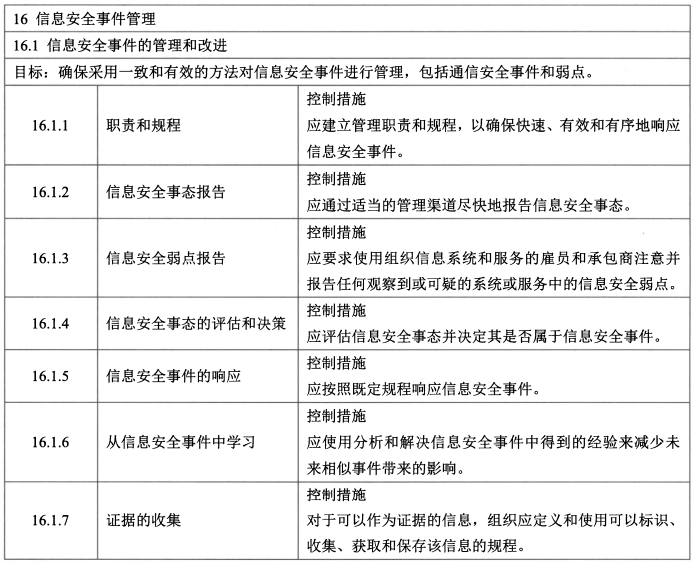
#### 12、信息安全事件管理(1/7)
|
||||
|
||||
@ -344,7 +344,7 @@
|
||||
- 从信息安全事件中学习
|
||||
- 证据的收集
|
||||
|
||||
|
||||

|
||||
|
||||
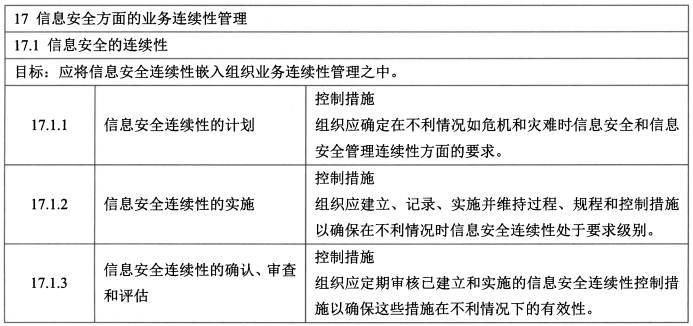
#### 13、业务连续性管理(2/4)
|
||||
|
||||
@ -354,7 +354,7 @@
|
||||
|
||||
- 控制措施:信息安全连续性的计划、信息安全连续性的实施、<span style="color:blue;">信息安全连续性的确认、审查和评估</span>。
|
||||
|
||||
|
||||

|
||||
|
||||
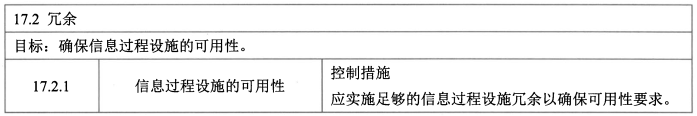
- **冗余 - 1**
|
||||
|
||||
@ -362,7 +362,7 @@
|
||||
|
||||
- 控制措施:信息过程设施的可用性。
|
||||
|
||||
|
||||

|
||||
|
||||
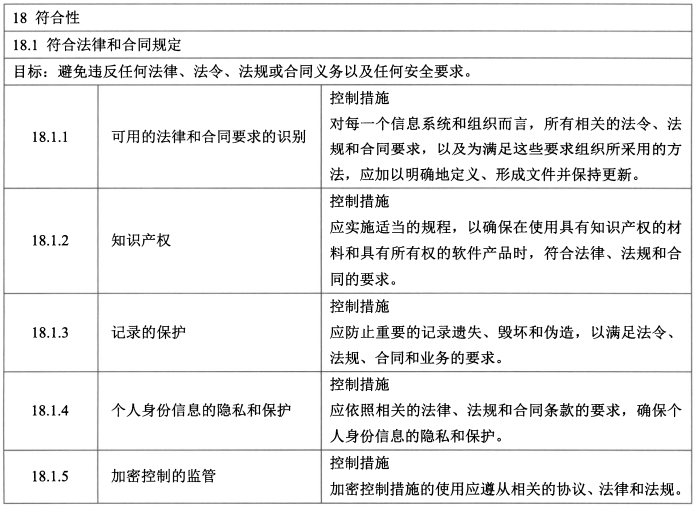
#### 14、符合性(2/8)
|
||||
|
||||
@ -372,7 +372,7 @@
|
||||
|
||||
- 控制措施:可用法律和合同要求的识别、知识产权、记录的保护、个人身份信息的隐私和保护、加密控制的监管。
|
||||
|
||||
|
||||

|
||||
|
||||
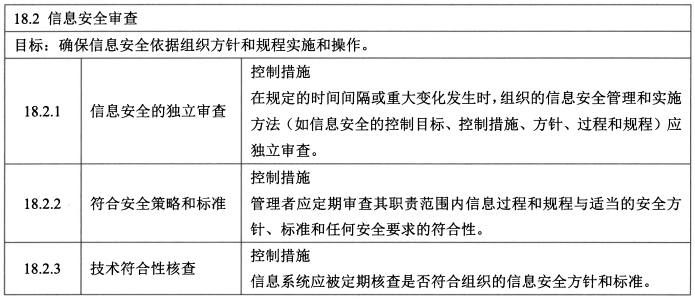
- **信息安全审核 - 3**
|
||||
|
||||
@ -380,7 +380,7 @@
|
||||
|
||||
- 控制措施:信息安全的独立审核、符合安全策略和标准、技术符合性核查。
|
||||
|
||||
|
||||

|
||||
|
||||
> <span style="background-color:yellow;">组织在规定的时间间隔(一般是一年)或重大变化发生时,组织的信息安全管理和实施方法(如信息安全的控制目标、控制措施、方针、过程和规程)应独立审查。<span style="color:red;">独立评审宜由管理者启动,由独立于被评审范围的人员执行</span></span>,例如<span style="color:blue;">交叉审核</span>(审核员A审查B的信息安全管理工作)、内部审核部门、独立的管理人员或专门进行这种评审的第三方组织。从事这些评审的人员宜具备适当的技能和经验。<span style="background-color:yellow;">内部审查的结果应该形成正式文件并长期留存。</span>
|
||||
|
||||
|
||||
@ -13,7 +13,7 @@
|
||||
|
||||
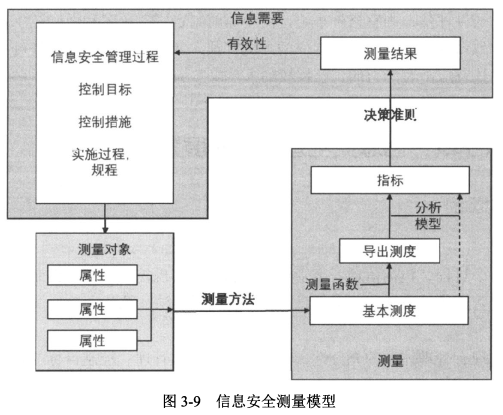
#### 1、测量模型
|
||||
|
||||
|
||||

|
||||
|
||||
### 二、测量要求与实现
|
||||
|
||||
|
||||
@ -81,7 +81,7 @@ BCM是找出组织有潜在影响的威胁及其对组织业务运行的影响
|
||||
3. 影响分析
|
||||
- 资产优先级划分
|
||||
|
||||
|
||||

|
||||
|
||||
1. **确定业务优先级**
|
||||
|
||||
|
||||
@ -57,7 +57,7 @@
|
||||
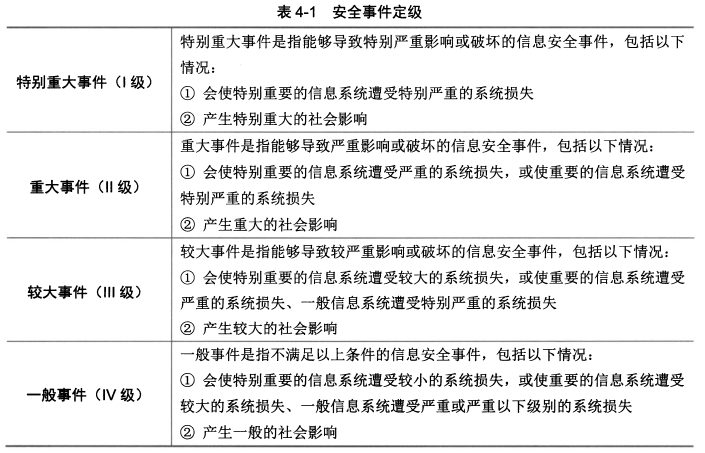
- 较大事件(Ⅲ级)
|
||||
- 一般事件(Ⅳ级)
|
||||
|
||||
|
||||

|
||||
|
||||
#### 3、信息安全应急响应组织
|
||||
|
||||
@ -81,7 +81,7 @@
|
||||
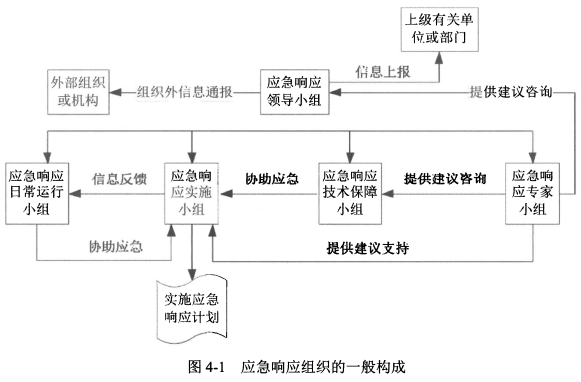
- 应急响应实施组
|
||||
- 应急响应日常运行组
|
||||
|
||||
|
||||

|
||||
|
||||
### 二、网络安全应急响应预案
|
||||
|
||||
@ -123,7 +123,7 @@
|
||||
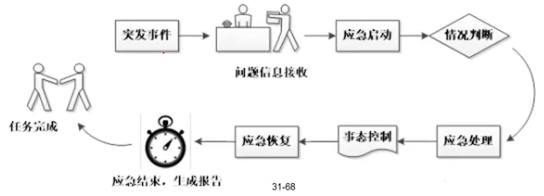
- 应急响应事件<span style="color:red;">后期运维</span>
|
||||
- <span style="color:red;">更新</span>现有应急预案
|
||||
|
||||
|
||||

|
||||
|
||||
### 三、计算机取证与保全
|
||||
|
||||
@ -141,7 +141,7 @@
|
||||
|
||||
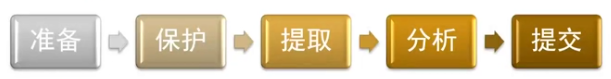
#### 3、取证流程
|
||||
|
||||
|
||||

|
||||
|
||||
1. **准备阶段**
|
||||
|
||||
|
||||
@ -62,7 +62,7 @@
|
||||
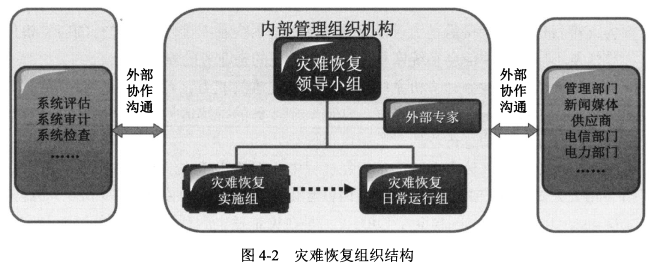
- 领导组、规划实施组、日常运行组
|
||||
- 规划工作可聘请外部专家,实实施和运行也可委托外包机构承担
|
||||
|
||||
|
||||

|
||||
|
||||
#### 6、国家灾备政策及相关标准
|
||||
|
||||
@ -96,7 +96,7 @@
|
||||
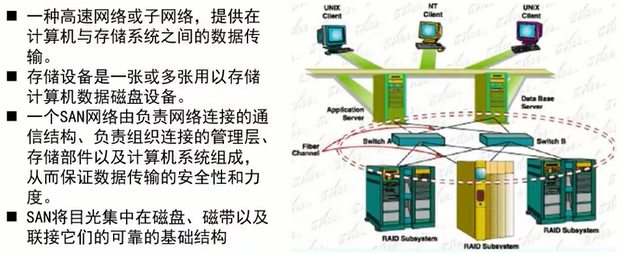
- 专用网络、效率高、扩展方便
|
||||
- 成本高、实施复杂、难度大
|
||||
|
||||
|
||||

|
||||
|
||||
#### 2、备份技术
|
||||
|
||||
@ -108,7 +108,7 @@
|
||||
|
||||
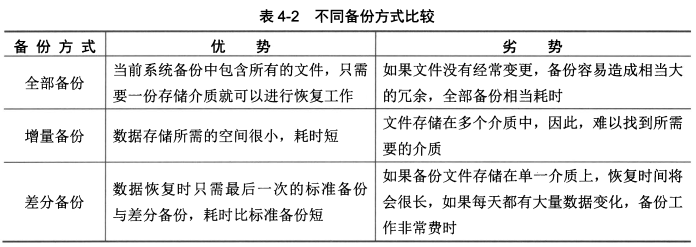
> 在备份技术中,主要包含<span style="color:red;">全部备份</span>、<span style="color:red;">增量备份</span>和<span style="color:red;">差分备份</span>3种备份方式:<br><span style="background-color:yellow;"><span style="color:red;">①</span> 全部备份</span>是对整个系统所有文件进行完全备份,包括所有系统和数据;<br><span style="background-color:yellow;"><span style="color:red;">②</span> 增量备份</span>是每次备份的数据相当于上一次备份后增加和修改过的数据;<br><span style="background-color:yellow;"><span style="color:red;">③ </span>差分备份</span>是每次备份的数据相对于上一次全部备份之后新增加和修改过的数据。
|
||||
|
||||
|
||||

|
||||
|
||||
2. **备份介质**
|
||||
|
||||
@ -125,7 +125,7 @@
|
||||
|
||||
4. **备用场所**
|
||||
|
||||

|
||||

|
||||
|
||||
### 三、灾难恢复策略
|
||||
|
||||
@ -171,7 +171,7 @@
|
||||
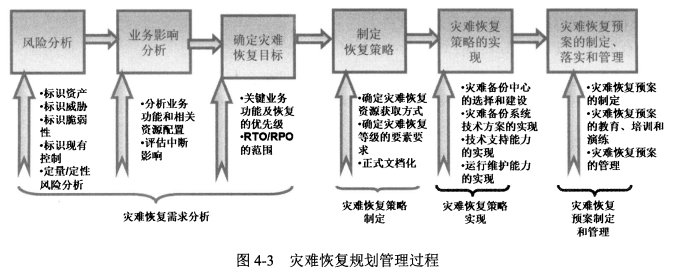
- 灾难恢复<span style="color:red;">策略实现</span>
|
||||
- 灾难恢复<span style="color:red;">预案的制定和管理</span>
|
||||
|
||||
|
||||

|
||||
|
||||
#### 2、灾难恢复需求分析
|
||||
|
||||
@ -194,16 +194,16 @@
|
||||
|
||||
- <span style="background-color:yellow;">选择和建设灾难备份中心(考点)</span>
|
||||
|
||||

|
||||

|
||||
|
||||
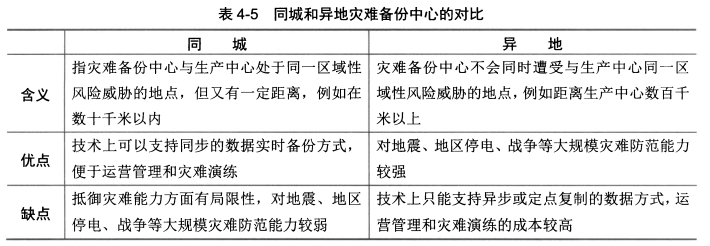
- 选择或建设灾难备份中心,<span style="background-color:yellow;">应遵循一般的选址原则</span>。
|
||||
选择或建设灾难备份中心时,应根据风险评估的结果,<span style="background-color:yellow;">避免灾难备份中心与生产中心同时遭受同类风险</span>。根据规避灾难风险影响范围的不同,<span style="background-color:yellow;">灾难备份中心分同城和异地两种类型</span>,二者的对比如下所示。
|
||||
|
||||
|
||||

|
||||
|
||||
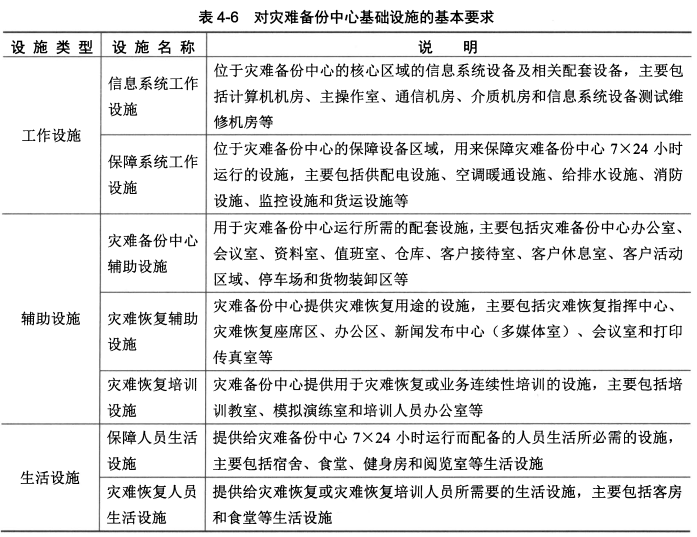
- 工作设施、辅助设施和生活设施应符合灾难恢复目标的要求,主要包括表4-6中说明的几个方面。
|
||||
|
||||
|
||||

|
||||
|
||||
- 实现灾难备份系统技术方案
|
||||
|
||||
|
||||
@ -35,7 +35,7 @@
|
||||
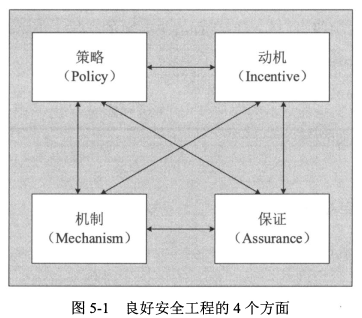
- 保证
|
||||
- 动机
|
||||
|
||||
|
||||

|
||||
|
||||
#### 2、为什么需要系统安全工程
|
||||
|
||||
@ -75,7 +75,7 @@
|
||||
|
||||
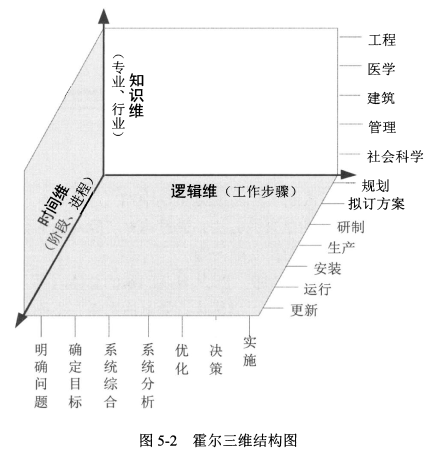
- 知识维
|
||||
|
||||
|
||||

|
||||
|
||||
#### 4、项目管理
|
||||
|
||||
@ -152,7 +152,7 @@
|
||||
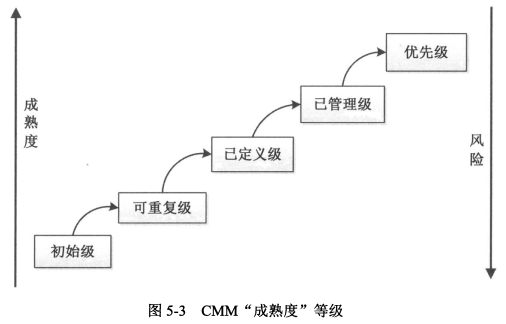
- 工程实施组织的能力成熟度<span style="color:red;">等级越高</span>,系统的<span style="color:red;">风险越低</span>。
|
||||
- CMM为工程的过程能力提供了一个阶梯式的<span style="color:red;">改进框架</span>。
|
||||
|
||||
|
||||

|
||||
|
||||
### 三、系统安全工程能力成熟度模型
|
||||
|
||||
@ -184,7 +184,7 @@
|
||||
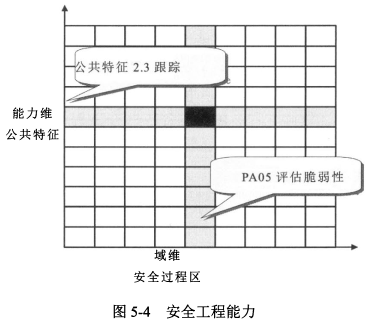
- <span style="color:red;">"域维"</span>由所有定义的安全工程<span style="color:red;">过程区域</span>构成
|
||||
- <span style="color:red;">"能力维"</span>代表组织实施这一过程的能力
|
||||
|
||||
|
||||

|
||||
|
||||
#### 4、域维—过程区域
|
||||
|
||||
@ -207,7 +207,7 @@
|
||||
|
||||
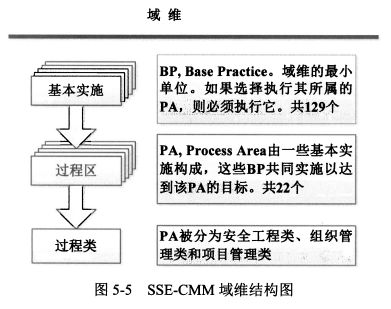
- SSE-CMM包含22个PA,分为<span style="color:red;">工程</span>、<span style="color:red;">项目</span>、<span style="color:red;">组织</span>三类
|
||||
|
||||
|
||||

|
||||
|
||||
#### 5、能力维—过程能力
|
||||
|
||||
@ -221,7 +221,7 @@
|
||||
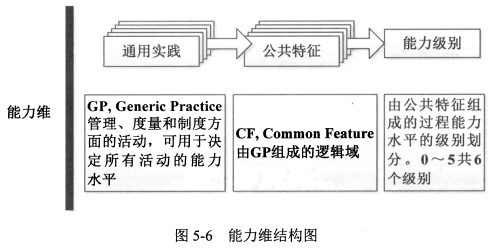
- <span style="color:red;">成熟度低</span>,成本、进度、功能和质量都不稳定;
|
||||
- <span style="color:red;">成熟度高</span>,达到预定的成本、进度、功能和质量目标的就越有把握。
|
||||
|
||||
|
||||

|
||||
|
||||
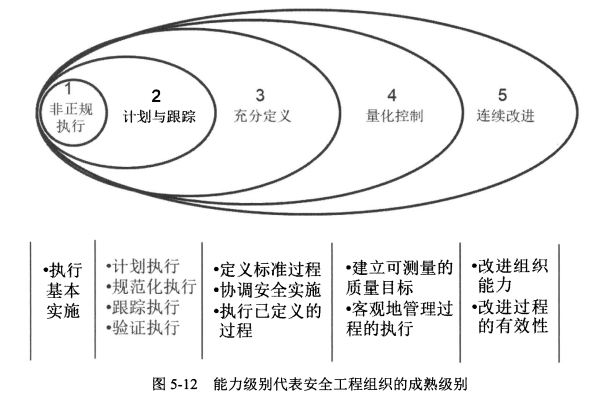
> <span style="color:red;">注意:</span>一个组织机构可随意以他们所选择的方式和次序来计划、跟踪、定义、控制和改进他们的过程。然而,由于一些较高级别的通用实施依赖于较低级别的通用实施,因此,<span style="background-color:yellow;">组织机构在试图达到较高级别之前,应首先实现较低级别通用实施。</span>
|
||||
|
||||
@ -231,7 +231,7 @@
|
||||
|
||||
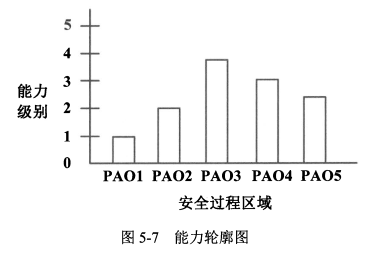
- 给每个PA赋予一个能力级别<span style="color:red;">评分</span>,所得到的两维图形便形象地反映一个工程组织整体上的系统安全工程<span style="color:red;">能力成熟度</span>,也间接的反映其工作结果的质量及其安全上的<span style="color:red;">可信度</span>。
|
||||
|
||||
|
||||

|
||||
|
||||
> 木桶理论,按最低的算。
|
||||
|
||||
@ -250,19 +250,19 @@
|
||||
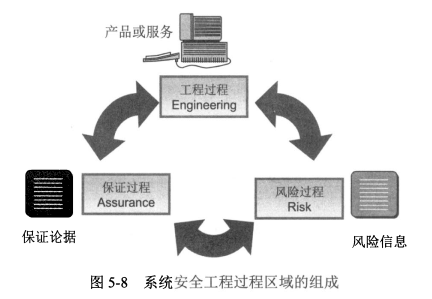
| <span style="background-color:red;">风险过程</span> 4个 | <span style="background-color:yellow;">工程过程</span> 5个 | <span style="background-color:lightgreen;">保证过程</span> 2个 |
|
||||
| -------------------------------------------------------- | ----------------------------------------------------------- | ------------------------------------------------------------ |
|
||||
|
||||

|
||||

|
||||
|
||||
#### 2、工程类过程之间关系
|
||||
|
||||
- 11个PA分为<span style="color:red;">风险过程</span>、<span style="color:red;">工程过程</span>、<span style="color:red;">保证过程</span>。
|
||||
|
||||
|
||||

|
||||
|
||||
#### 3、风险过程
|
||||
|
||||
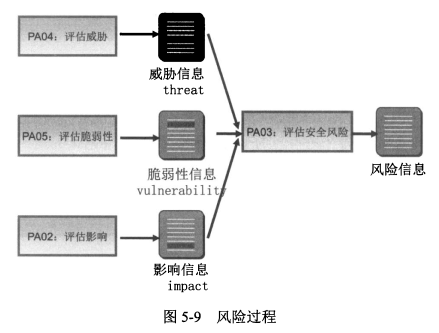
1. **调查和量化风险的过程**
|
||||
|
||||
|
||||

|
||||
|
||||
2. **PA04:评估威胁**
|
||||
|
||||
@ -313,7 +313,7 @@
|
||||
|
||||
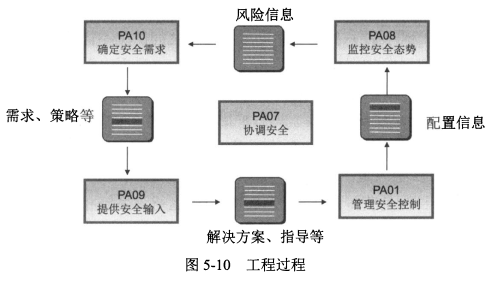
- SSE-CMM强调<span style="color:red;">安全工程师是一个大的项目队伍中的一部分</span>,需要与其它科目工程师的活动相互协调。
|
||||
|
||||
|
||||

|
||||
|
||||
1. **PA10:确定安全需求**
|
||||
|
||||
@ -374,7 +374,7 @@
|
||||
|
||||
- SSE-CMM的信任程度<span style="color:red;">来自于</span>安全工程过程<span style="color:blue;">可重复性</span>的结果质量。
|
||||
|
||||
|
||||

|
||||
|
||||
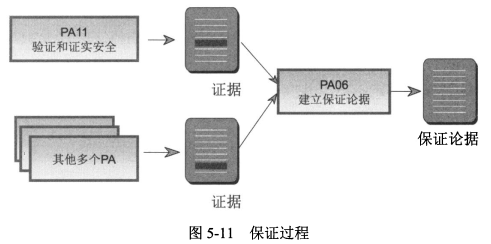
1. **PA11:验证和证实安全**
|
||||
|
||||
@ -400,7 +400,7 @@
|
||||
|
||||
- 组织的<span style="color:red;">过程管理</span>和<span style="color:red;">制度化能力</span>的强弱
|
||||
|
||||
|
||||

|
||||
|
||||
#### 1、能力级别—1级:<span style="color:red;">非正规执行级</span>
|
||||
|
||||
|
||||
@ -76,4 +76,5 @@
|
||||
- 减少或消除事件(包括IT事件和安全事件)对信息系统运行带来的干扰;
|
||||
- <span style="color:red;">检测事件</span>然后准确确定正确的支持资源以便尽快解决事件的能力;
|
||||
- 为管理层提供关于影响组织的事件的准确信息以便他们能够确定必需的支持资源,并为支持资源的供给做好计划;
|
||||
- <span style="color:red;">事件管理流程涉及运营的整个生命周期。</span>
|
||||
- <span style="color:red;">事件管理流程涉及运营的整个生命周期</span>。
|
||||
|
||||
|
||||
@ -70,7 +70,7 @@
|
||||
|
||||
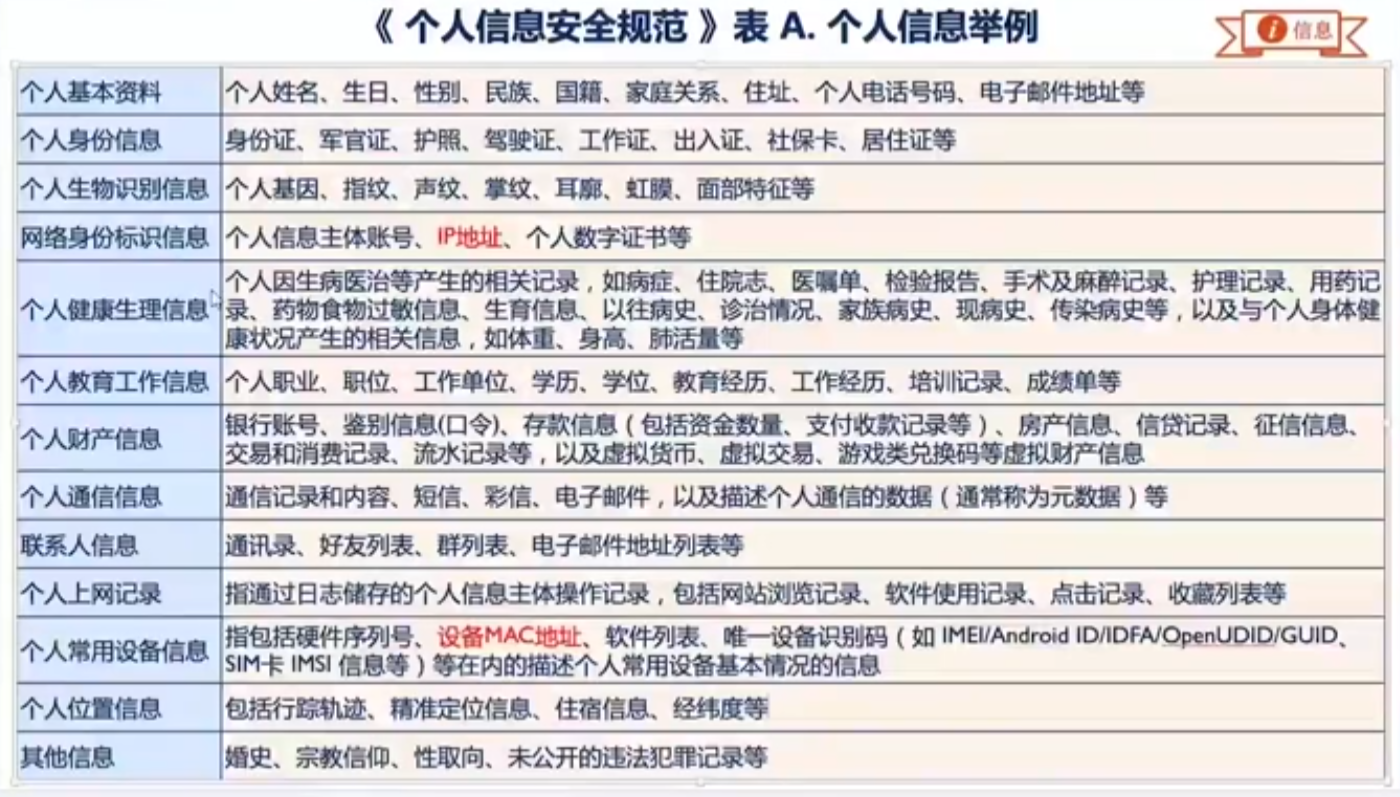
- 保护生日、年龄、E-mail邮件地址、手机号码、家庭电话号码等信息
|
||||
|
||||
|
||||

|
||||
|
||||
### 二、培训及教育
|
||||
|
||||
@ -88,4 +88,3 @@
|
||||
1. 首次加入组织时加以培训
|
||||
2. 定期接受最新的培训
|
||||
|
||||
|
||||
|
||||
@ -75,7 +75,7 @@
|
||||
|
||||
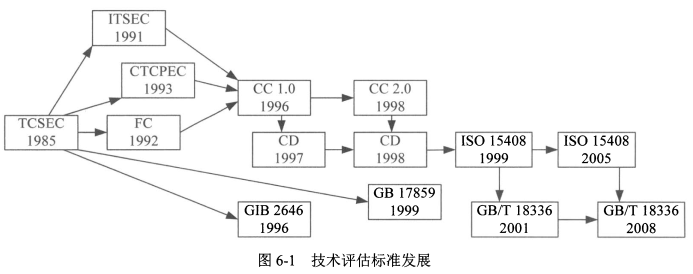
### 二、安全评估标准
|
||||
|
||||
|
||||

|
||||
|
||||
#### 1、TCSEC(可信计算机系统评估标准)
|
||||
|
||||
@ -170,11 +170,11 @@
|
||||
|
||||
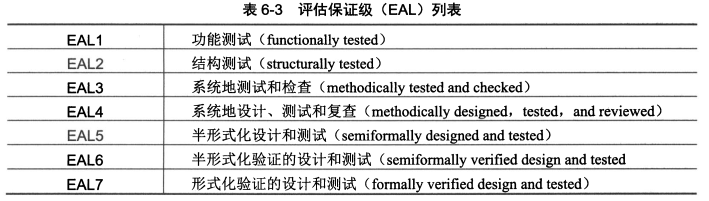
#### 7、评估保证级别(EAL)
|
||||
|
||||
|
||||

|
||||
|
||||
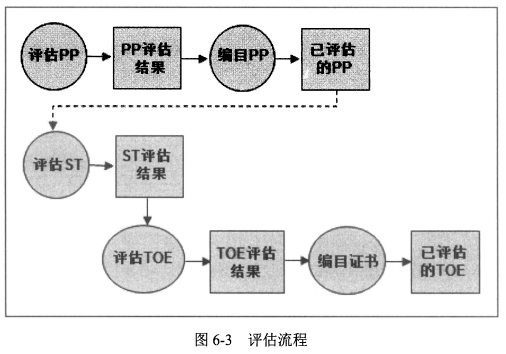
#### 8、评估流程
|
||||
|
||||
|
||||

|
||||
|
||||
#### 9、CC的意义
|
||||
|
||||
|
||||
@ -52,7 +52,7 @@
|
||||
|
||||
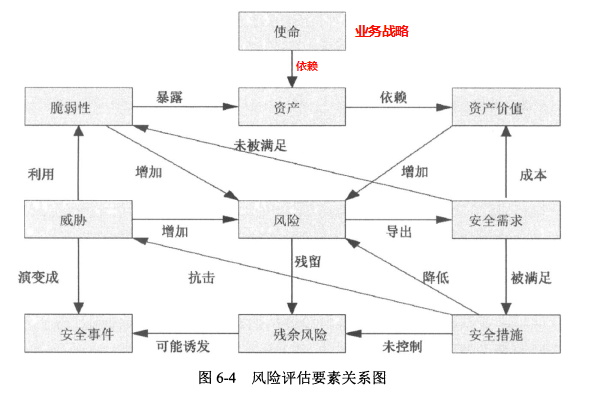
#### 5、风险评估要素之间关系
|
||||
|
||||
|
||||

|
||||
|
||||
### 二、风险评估途径与方式方法
|
||||
|
||||
@ -105,7 +105,7 @@
|
||||
|
||||
- 由上述条件可计算风险组织的年度预期损失及ROSI为组织提供一个良好的风险管理财务清单。
|
||||
|
||||

|
||||

|
||||
|
||||
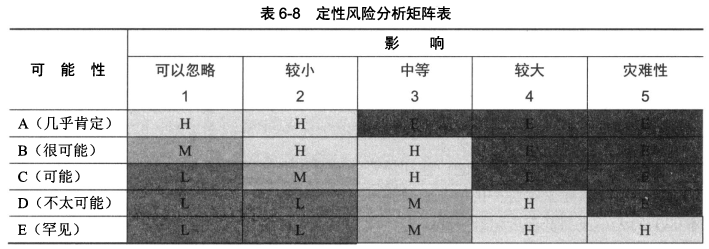
- 定性分析
|
||||
|
||||
@ -113,7 +113,7 @@
|
||||
|
||||
- 带有很强的<span style="color:red;">主观性</span>,往往凭借分析者的经验和直觉,或者业界的标准和惯例,为风险管理诸要素的大小或高低程度定性分级。
|
||||
|
||||
|
||||

|
||||
|
||||
### 三、风险评估基本过程
|
||||
|
||||
@ -121,7 +121,7 @@
|
||||
|
||||
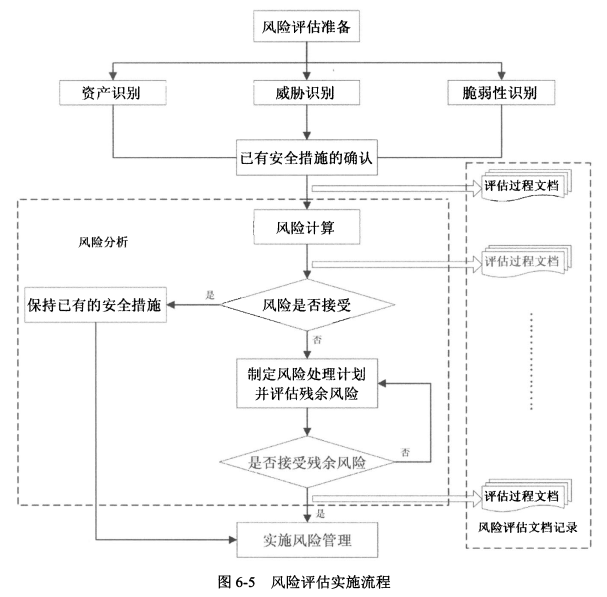
- <span style="color:red;">风险评估</span>是组织确定信息安全需求的过程,包括资产识别与评价、威胁和弱点评估、控制措施评估、风险认定在内的<span style="color:red;">一系列活动</span>。
|
||||
|
||||
|
||||

|
||||
|
||||
#### 2、风险评估准备
|
||||
|
||||
@ -179,7 +179,7 @@
|
||||
|
||||
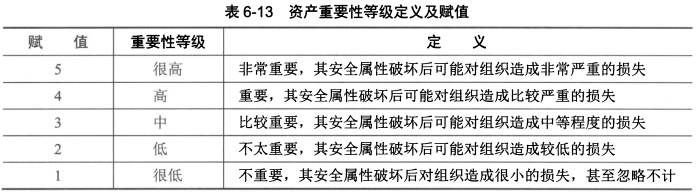
- 依据资产价值大小对资产的重要性划分不同的等级资产价值依据资产在保密性、完整性和可用性上的赋值等级,经过综合评定得出。
|
||||
|
||||
|
||||

|
||||
|
||||
#### 4、威胁识别
|
||||
|
||||
@ -189,7 +189,7 @@
|
||||
|
||||
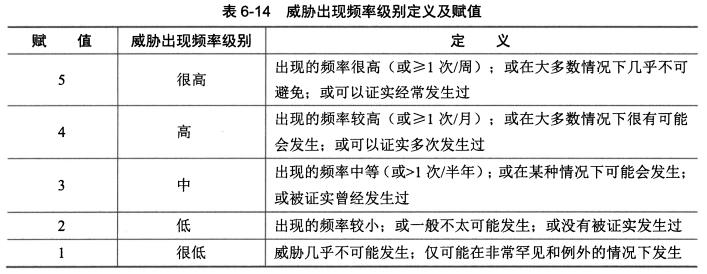
- 威胁频率级别
|
||||
|
||||
|
||||

|
||||
|
||||
#### 5、脆弱性识别
|
||||
|
||||
@ -203,7 +203,7 @@
|
||||
|
||||
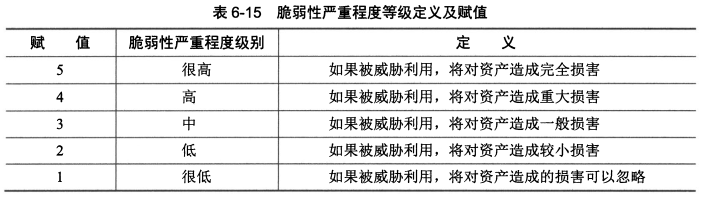
- 脆弱性识别的方法有哪些?
|
||||
|
||||
|
||||

|
||||
|
||||
#### 6、确认已有的控制措施
|
||||
|
||||
@ -231,7 +231,7 @@
|
||||
|
||||
> 最新:GB/T 20984-2022
|
||||
|
||||
|
||||

|
||||
|
||||
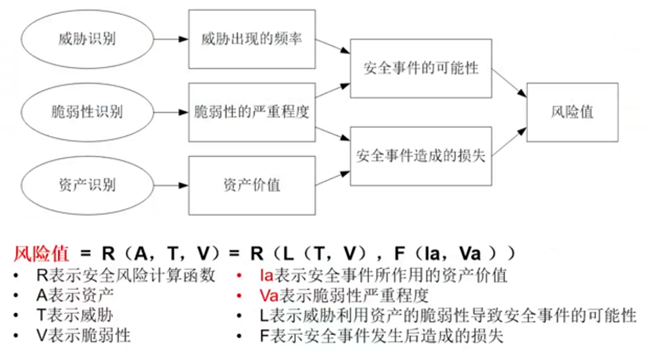
- 计算安全事件发生的可能性
|
||||
|
||||
@ -255,7 +255,7 @@
|
||||
|
||||
- 汇总各项输出文档和《风险程度等级列表》,综合评价风险状况,形成《风险评估报告》。
|
||||
|
||||
|
||||

|
||||
|
||||
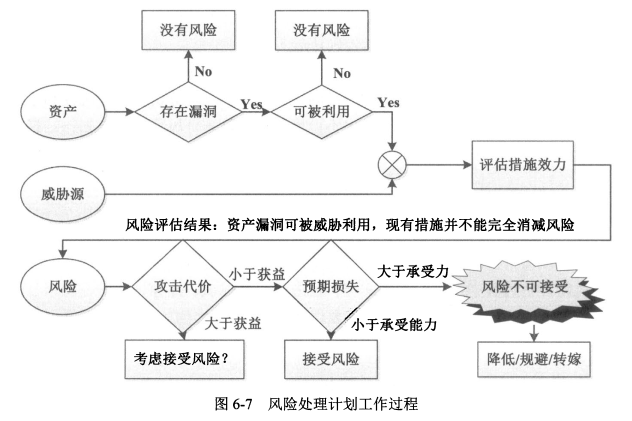
#### 9、风险处理计划
|
||||
|
||||
@ -264,7 +264,7 @@
|
||||
- 管理措施
|
||||
- 技术措施
|
||||
|
||||
|
||||

|
||||
|
||||
#### 10、残余风险评估
|
||||
|
||||
@ -274,7 +274,7 @@
|
||||
|
||||
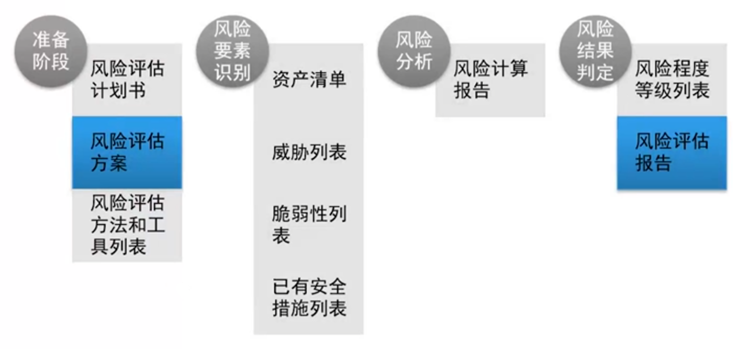
### 四、风险评估文档
|
||||
|
||||
|
||||

|
||||
|
||||
#### 1、准备阶段
|
||||
|
||||
|
||||
@ -37,7 +37,7 @@
|
||||
- 报告起草和执行
|
||||
- 问题跟踪
|
||||
|
||||
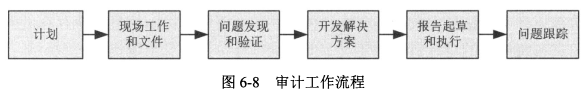
|
||||

|
||||
|
||||
### 二、审计技术控制
|
||||
|
||||
|
||||
@ -63,7 +63,7 @@
|
||||
- 明文、密文
|
||||
- 加密、解密、加密密钥、解密密钥
|
||||
|
||||
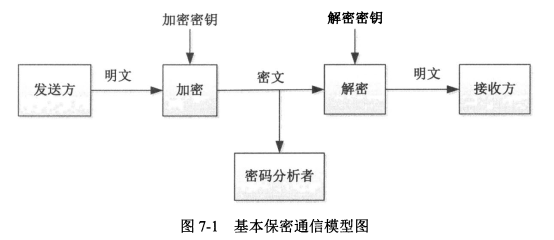
|
||||

|
||||
|
||||
#### 6、密码系统的安全性
|
||||
|
||||
@ -82,7 +82,7 @@
|
||||
|
||||
#### 7、<span style="background-color:yellow;">密码学技术在信息安全中的应用</span>
|
||||
|
||||
|
||||

|
||||
|
||||
#### 8、分组密码与流密码
|
||||
|
||||
@ -106,7 +106,7 @@
|
||||
|
||||
- <span style="color:red;">不足</span>:安全交换密钥问题及密钥管理复杂
|
||||
|
||||
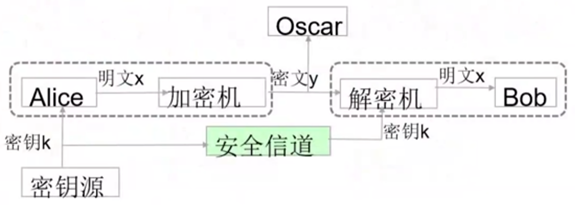
|
||||

|
||||
|
||||
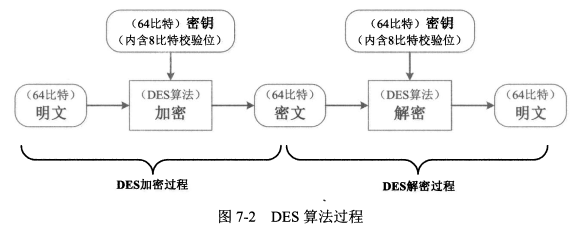
#### 2、DES 和 3DES
|
||||
|
||||
@ -116,7 +116,7 @@
|
||||
|
||||
- DES算法把64位的明文输入块变为<span style="color:red;">64位</span>的密文输出块,它所使用的<span style="color:red;">密钥也是64位</span>(有效密钥为56位,第8、16、24、32、40、48、56、64位是校验位,使得每个密钥都有奇数个1)。
|
||||
|
||||
|
||||

|
||||
|
||||
- 3DES:该方法使用两个密钥,执行3次DES算法,加密的过程是加密 - 解密 - 加密,解密的过程是解密 - 加密 - 解密。
|
||||
|
||||
@ -205,7 +205,7 @@
|
||||
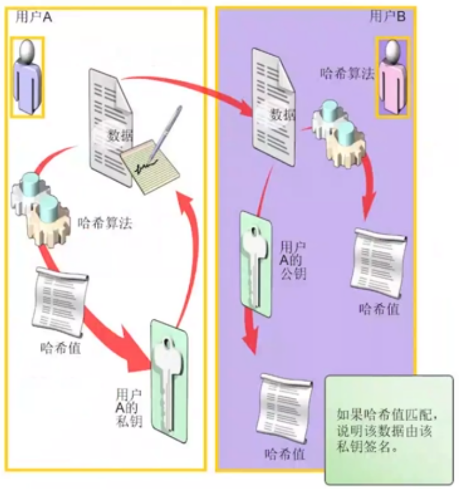
- 发送过程
|
||||
- 接收过程
|
||||
|
||||
|
||||

|
||||
|
||||
### 五、公钥基础设施
|
||||
|
||||
@ -220,7 +220,7 @@
|
||||
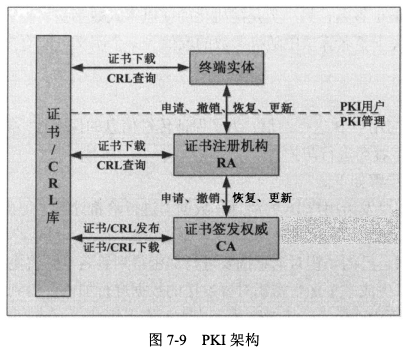
- 证书存放管理(目录服务)
|
||||
- 终端实体(证书持有者和应用程序)
|
||||
|
||||
|
||||

|
||||
|
||||
#### 3、CA:认证权威
|
||||
|
||||
@ -267,3 +267,5 @@
|
||||
|
||||
#### 7、PKI/CA技术的典型应用
|
||||
|
||||
> 略
|
||||
|
||||
|
||||
@ -83,7 +83,7 @@
|
||||
|
||||
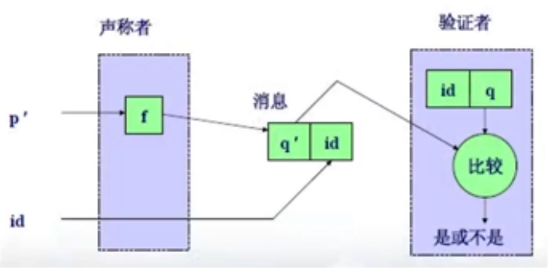
- 加密:单单向函数
|
||||
|
||||
|
||||

|
||||
|
||||
- 攻击者很容易构造一张a与p对应的表,表中的p尽可能包含所期望的值
|
||||
|
||||
@ -107,7 +107,7 @@
|
||||
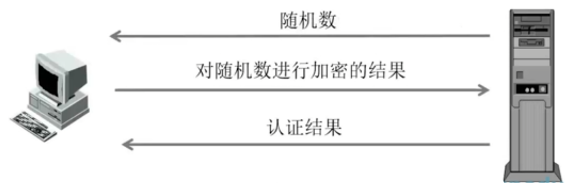
- 将登录信息(用户名、密码)与随机数合并,使用单向函数(如MD5)生产字符串,作为应答返回服务器
|
||||
- 服务认证后返还结果
|
||||
|
||||
|
||||

|
||||
|
||||
### 三、基于实体所有的鉴别
|
||||
|
||||
@ -146,7 +146,7 @@
|
||||
|
||||
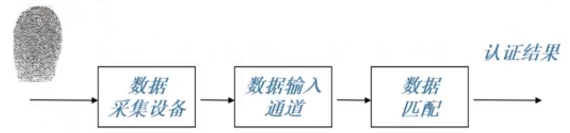
- 使用每个人所具有的唯一生理特征
|
||||
|
||||
|
||||

|
||||
|
||||
- 鉴别的方式
|
||||
|
||||
@ -162,7 +162,7 @@
|
||||
|
||||
3. 静脉:个人静脉分布图(指静脉、掌静脉)。
|
||||
|
||||
|
||||

|
||||
|
||||
- <span style="color:red;">虹膜、视网膜</span>
|
||||
|
||||
@ -193,7 +193,7 @@
|
||||
|
||||
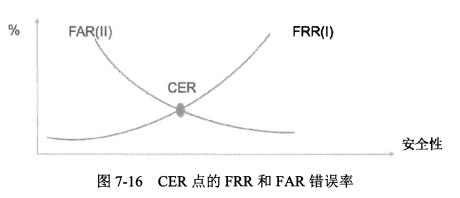
- 交叉错判率(CER):FRR=FAR的交叉点,CER用来反映系统的准确度
|
||||
|
||||
|
||||

|
||||
|
||||
### 五、Kerberos体系
|
||||
|
||||
@ -246,7 +246,7 @@
|
||||
- 第二次:获得服务许可票据(SGT)
|
||||
- 第三次:获得服务
|
||||
|
||||
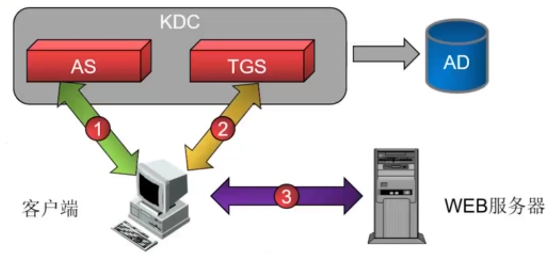
|
||||

|
||||
|
||||
#### 5、Kerberos工作过程
|
||||
|
||||
@ -261,7 +261,7 @@
|
||||
- TGT(包含TGS会话密钥),使用KDC密码加密;
|
||||
- 其他信息(包含TGS会话密钥),使用用户密码加密。
|
||||
|
||||

|
||||

|
||||
|
||||
2. **获得SGT**
|
||||
|
||||
@ -273,7 +273,7 @@
|
||||
- SGT
|
||||
- 客户机与应用服务器之间的会话密钥
|
||||
|
||||

|
||||

|
||||
|
||||
3. **获得服务**
|
||||
|
||||
@ -283,7 +283,7 @@
|
||||
- 应用服务器(验证认证信息)
|
||||
- 提供服务器验证信息(如果需要验证服务器)
|
||||
|
||||

|
||||

|
||||
|
||||
### 六、认证、授权和计费
|
||||
|
||||
|
||||
@ -47,11 +47,11 @@
|
||||
- 访问权限是指主体对客体所执行的操作;
|
||||
- 对目录的访问模式可以分为读和写*(没有拒绝)*。
|
||||
|
||||
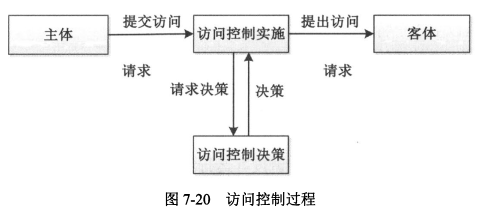
|
||||

|
||||
|
||||
#### 4、访问控制模型的分类
|
||||
|
||||
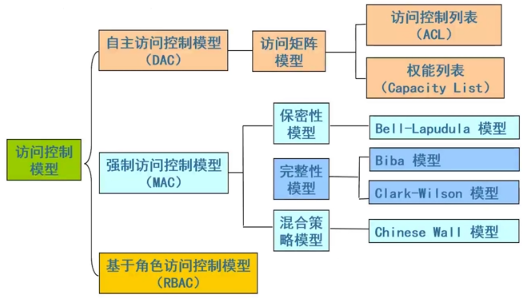
|
||||

|
||||
|
||||
### 二、自主访问控制模型
|
||||
|
||||
@ -65,7 +65,7 @@
|
||||
|
||||
- 访问控制表/矩阵
|
||||
|
||||
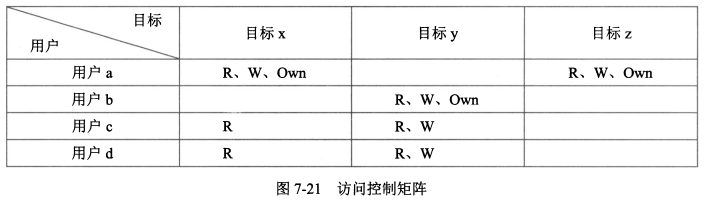
|
||||

|
||||
|
||||
#### 3、实现方式
|
||||
|
||||
@ -74,14 +74,14 @@
|
||||
- 权限与客体关联;
|
||||
- 在客体上附加一个主体明细表的方法来表示访问控制矩阵的。
|
||||
|
||||
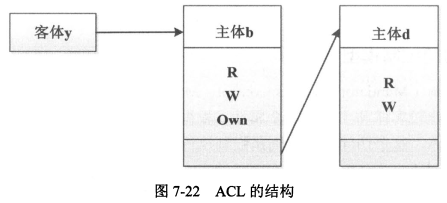
|
||||

|
||||
|
||||
- 访问能力表
|
||||
|
||||
- 权限与主体关联;
|
||||
- 为每个用户维护一个表,表示主体可以访问的客体及权限。
|
||||
|
||||
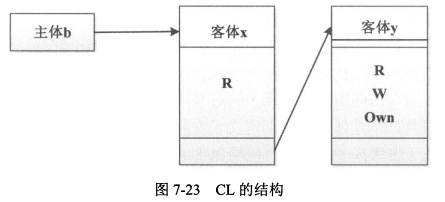
|
||||

|
||||
|
||||
#### 4、自主访问控制的特点
|
||||
|
||||
@ -167,7 +167,7 @@
|
||||
- 银行COI类(银行a、银行b、银行c)
|
||||
- 石油公司COI类(公司W、公司x、公司u、公司v)
|
||||
|
||||
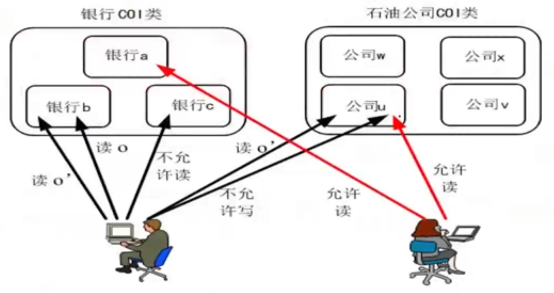
|
||||

|
||||
|
||||
### 四、基于角色的访问控制模型
|
||||
|
||||
@ -190,7 +190,7 @@
|
||||
- RBAC2:包含RBACO,加入约束条件,例如财务和会计不能为同一人;
|
||||
- RBAC3:结合了RBAC1、RBAC2。
|
||||
|
||||
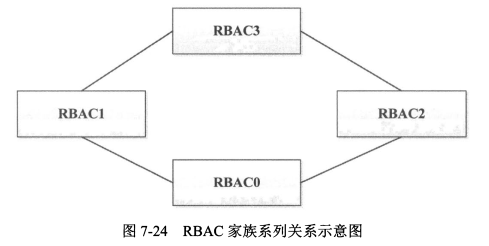
|
||||

|
||||
|
||||
- <span style="background-color:yellow;">特点</span>
|
||||
|
||||
|
||||
@ -88,9 +88,9 @@
|
||||
|
||||
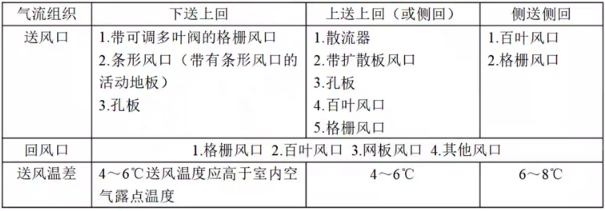
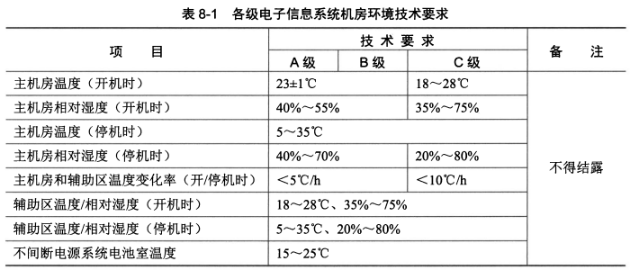
> 普通空调系统无法满足机房运营保障,需要使用机房专用的精密空。
|
||||
|
||||
|
||||

|
||||
|
||||
|
||||

|
||||
|
||||
#### 7、电磁防护
|
||||
|
||||
|
||||
@ -23,7 +23,7 @@
|
||||
|
||||
- 处理用户服务和各种应用请求包括<span style="color:red;">会话层</span>、<span style="color:red;">表示层</span>、<span style="color:red;">应用层</span>。
|
||||
|
||||

|
||||

|
||||
|
||||
### 二、OSI模型通信过程
|
||||
|
||||
@ -36,11 +36,11 @@
|
||||
|
||||
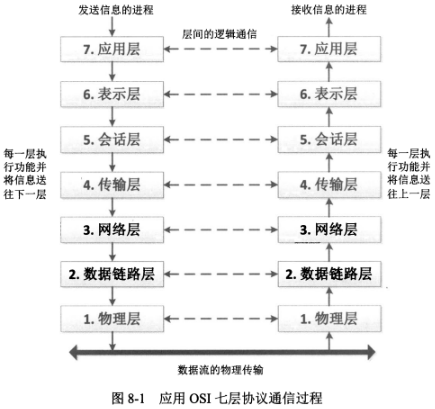
#### 2、数据封装与分用(解封装)
|
||||
|
||||
|
||||

|
||||
|
||||
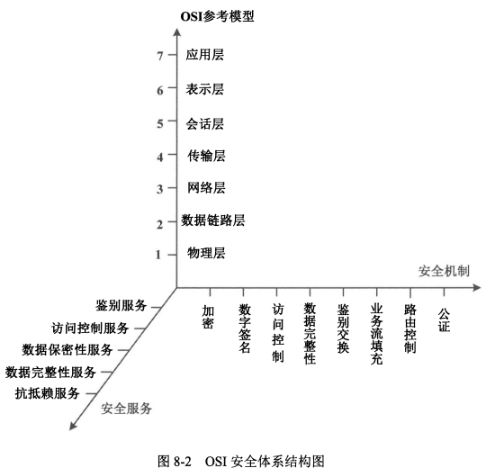
### 三、OSI七层模型安全体系
|
||||
|
||||
|
||||

|
||||
|
||||
#### 1、目标
|
||||
|
||||
|
||||
@ -15,7 +15,7 @@
|
||||
|
||||
#### 1、TCP/IP协议结构
|
||||
|
||||
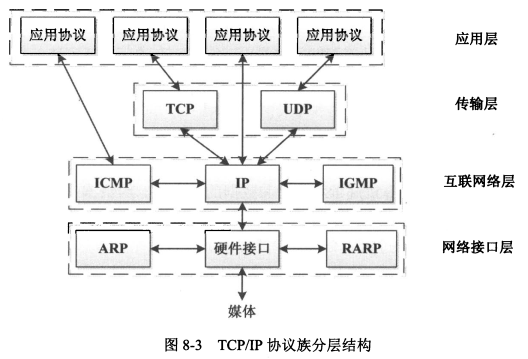
|
||||

|
||||
|
||||
#### 2、网络接口层
|
||||
|
||||
@ -40,7 +40,7 @@
|
||||
- IP是TCP/IP协议族中最为核心的协议
|
||||
- 目前广泛使用的IPv4提供<span style="color:red;">无连接</span><span style="color:blue;">不可靠</span>的服务
|
||||
|
||||
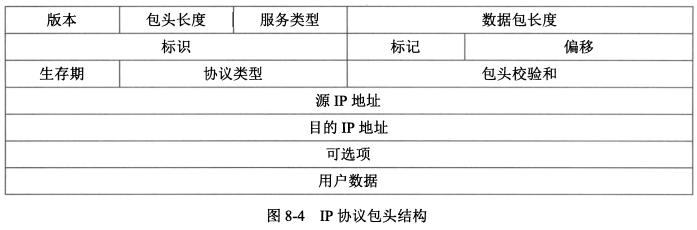
|
||||

|
||||
|
||||
2. **IP地址的分类**
|
||||
|
||||
@ -79,7 +79,7 @@
|
||||
|
||||
- ......
|
||||
|
||||
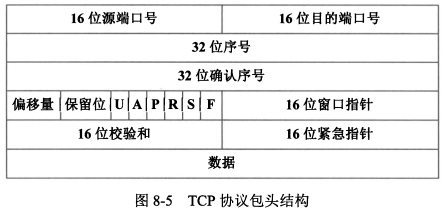
|
||||

|
||||
|
||||
2. **UDP(用户数据报协议)**
|
||||
|
||||
@ -89,7 +89,7 @@
|
||||
- 协议简单、占用资源少,效率高
|
||||
- ......
|
||||
|
||||
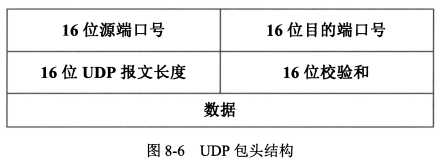
|
||||

|
||||
|
||||
3. **安全问题**
|
||||
|
||||
@ -126,7 +126,7 @@
|
||||
|
||||
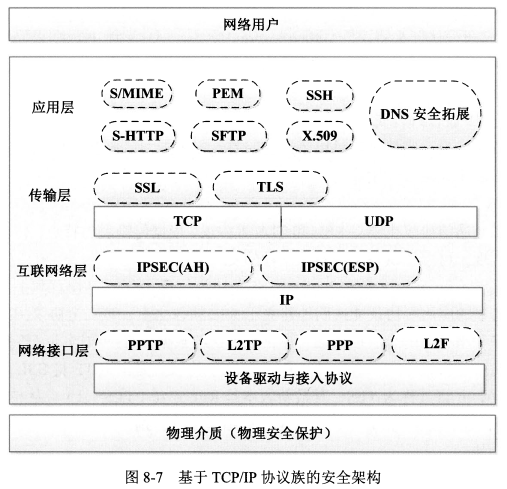
#### 1、基于TCP/IP协议簇的安全架构
|
||||
|
||||
|
||||

|
||||
|
||||
- IPSec协议通过认证头协议(Authentication Header,AH)为IP数据报提供无连接完整性与数据源认证,并提供保护以避免重播情况。
|
||||
- IPSec协议中通过封装安全载荷协议(Encapsulating Security Payload,ESP)加密需要保护的载荷数据,为这些数据提供机密性和完整性保护能力。
|
||||
@ -136,38 +136,3 @@
|
||||
> 略
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@ -69,7 +69,7 @@
|
||||
|
||||
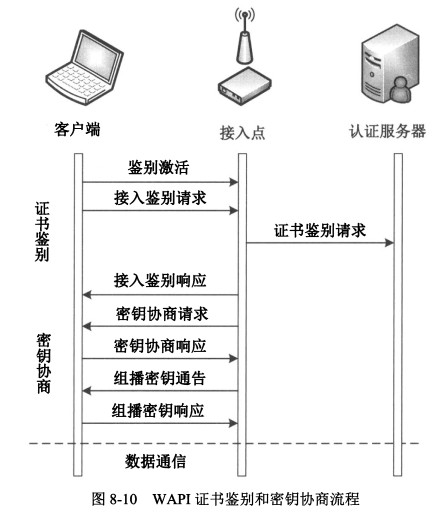
3. **WAPI证书鉴别和密钥协商流程**
|
||||
|
||||
|
||||

|
||||
|
||||
#### 4、无线局域网应用安全策略
|
||||
|
||||
|
||||
@ -26,13 +26,13 @@
|
||||
- ARP实现:ARP缓存。
|
||||
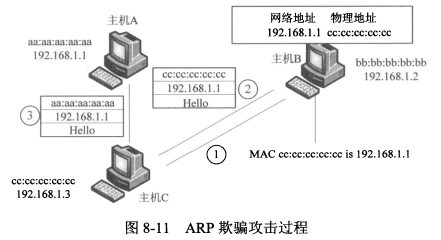
- ARP欺骗攻击过程
|
||||
|
||||
|
||||

|
||||
|
||||
#### 4、IP欺骗
|
||||
|
||||
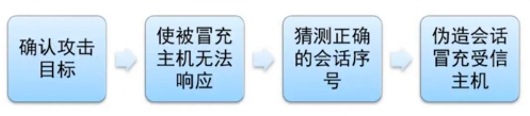
- IP欺骗是一系列步骤构成的攻击
|
||||
|
||||
|
||||

|
||||
|
||||
#### 5、DNS欺骗
|
||||
|
||||
@ -62,7 +62,7 @@
|
||||
|
||||
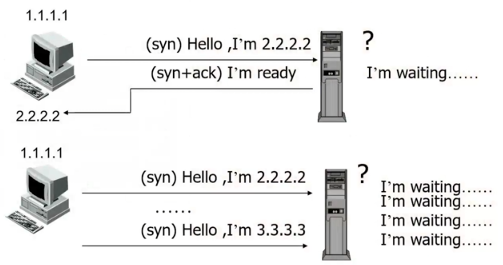
- 原理:伪造虚假地址连接请求,消耗主机连接数。
|
||||
|
||||
|
||||

|
||||
|
||||
#### 4、UDP Flood
|
||||
|
||||
@ -74,7 +74,7 @@
|
||||
|
||||
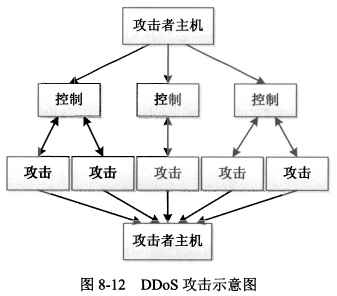
#### 6、分布式拒绝服务攻击(DDoS)
|
||||
|
||||
|
||||

|
||||
|
||||
#### 7、拒绝服务攻击的防御
|
||||
|
||||
|
||||
@ -19,7 +19,7 @@
|
||||
- <span style="color:red;">隔离</span>:将需要保护的网络与不可信任网络进行隔离,隐藏信息并进行安全防护。
|
||||
- <span style="color:red;">记录</span>:对进出数据进行检查,记录相关信息。
|
||||
|
||||
|
||||

|
||||
|
||||
#### 2、防火墙的主要技术
|
||||
|
||||
|
||||
@ -1,19 +1,222 @@
|
||||
# 操作系统安全
|
||||
|
||||
>
|
||||
> **一、操作系统安全机制**<br>
|
||||
> <span style="color:green;">了解</span>操作系统标识与鉴别、访问控制、权限管理信道保护、安全审计、内存存取、文件保护等安全机制;
|
||||
>
|
||||
> **二、操作系统安全配置**<br>
|
||||
> <span style="color:green;">了解</span>安全补丁、最小化部署、远程访问控制、账户及口令策略、安全审计及其他操作系统配置要点。
|
||||
|
||||
### 一、操作系统安全机制
|
||||
|
||||
#### 1、基础概念
|
||||
|
||||
1. **操作系统<span style="color:red;">安全目标</span>**
|
||||
|
||||
- <span style="color:red;">标识</span>系统中的用户和进行身份<span style="color:red;">鉴别</span>;
|
||||
|
||||
- 依据系统安全策略对用户的操作进行<span style="color:red;">访问控制</span>,防止用户和外来入侵者对计算机资源的非法访问;
|
||||
|
||||
- <span style="color:red;">监督</span>系统运行的安全性;
|
||||
|
||||
- <span style="color:red;">保证</span>系统自身的安全和完整性。
|
||||
|
||||
2. **实现目标的<span style="color:red;">安全机制</span>**
|
||||
- 标识与鉴别、访问控制、最小特权管理、信道保护、安全审计、内存存取保护、文件系统保护等
|
||||
|
||||
3. **安全系统(OS / APP / DBMS)的五大特征**
|
||||
|
||||
- 身份验证:强制性登录
|
||||
|
||||
- 访问控制:分级访问
|
||||
|
||||
- 审计:不可抵赖性
|
||||
|
||||
- 机密性
|
||||
|
||||
- 完整性
|
||||
|
||||
#### 2、标识与鉴别
|
||||
|
||||
1. **Windows系统的标识**
|
||||
|
||||
- 安全主体(账户、计算机、服务等)
|
||||
- <span style="color:red;">安全标识符</span>(Security Identifier,SID)
|
||||
- 在Windows系统中是基于SID,而不是基于名字来识别对象的,SID在创建该对象时产生,一旦被使用就永远都不会重复。
|
||||
- 安全主体的代表(标识用户、组和计算机账户的唯一编码)
|
||||
- SID范例:S-1-5-21-1736401710-1141508419-1540318053-1000
|
||||
- SID尾数值500只分配给内置管理员
|
||||
|
||||
2. **Linux/Unix系统的标识**
|
||||
|
||||
- <span style="color:red;">安全主体</span>:用户标识号(User ID)
|
||||
|
||||
3. **Windows系统用户信息管理**
|
||||
|
||||
- 存储在注册表中,运行期锁定
|
||||
|
||||
- 操作权限System(操作系统中的最高权限),依靠系统服务进行访问
|
||||
|
||||
- 示例:Windows密码散列值(LM-Hash)
|
||||
|
||||
> Administrator:500:C8825DB10F2590EAAAD3B435B51404EE:683020925C5D8569C23AA724774CE6CC:::
|
||||
|
||||
4. **身份鉴别**
|
||||
|
||||
- 远程鉴别
|
||||
- SMB、LM、NTLM
|
||||
- 本地鉴别
|
||||
|
||||
5. **Linux系统用户信息管理**
|
||||
|
||||
- 用户帐号文件F(/etc/passwd)
|
||||
- 使用不可逆DES算法加密的用户密码散列(早期)
|
||||
- 文本格式、全局可读
|
||||
- 影子文件(/etc/shadow)
|
||||
- 存储存放用户密码散列、密码管理信息等
|
||||
- 文本格式,仅对root可读可写
|
||||
|
||||

|
||||
|
||||
#### 3、访问控制
|
||||
|
||||
1. **Windows的访问控制**
|
||||
|
||||
- <span style="color:red;">访问令牌</span>(包含SID和特权列表),以用户身份运行的进程都拥有该令牌的一个拷贝
|
||||
- <span style="color:red;">访问控制列表</span>(ACL),仅NTFS文件系统支持
|
||||
|
||||
2. **Linux下的访问控制**
|
||||
|
||||
- 需要文件系统格式支持
|
||||
|
||||
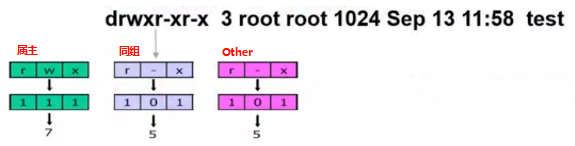
- 权限类型:读、写、执行(UGO管理机制)
|
||||
|
||||
- 权限表示方式:<span style="color:red;">模式位</span>
|
||||
|
||||
|
||||
|
||||
#### 4、权限管理
|
||||
|
||||
1. **Windows系统特权管理**
|
||||
|
||||
- 用户帐户控制(UAC)
|
||||
- 内置管理员可以把非内置管理员从管理员组中删除,而非内置管理员不能把内置管理员从管理员组中删除。
|
||||
- 标准受限访问令牌 & 完全访问令牌
|
||||
|
||||
2. **Linux系统特权管理**
|
||||
|
||||
- 限制对root使用,su及sudo命令
|
||||
|
||||
- <span style="color:red;">Suid位</span>:任何用户执行文件运行权限都为文件所有者的权限
|
||||
|
||||

|
||||
|
||||
#### 5、信道保护
|
||||
|
||||
1. **正常信道的保护**
|
||||
- 可信通路(Trusted Path)
|
||||
- 安全键(SAK)
|
||||
2. **隐蔽信道保护**
|
||||
- 隐蔽信道指利用系统中那些本来不是用于通信的系统资源绕过强制存取控制进行非法通信的一种机制。
|
||||
- 发现隐蔽信道
|
||||
- 共同访问权限;
|
||||
- 共同修改权限;
|
||||
- 接收进程可检资源的改变,而发送进程有权限改变;
|
||||
- 某种机制可启动通信并改变通信事件的顺序。
|
||||
|
||||
#### 6、安全审计
|
||||
|
||||
- 对系统中有关安全的活动进行<span style="color:red;">记录</span>、<span style="color:red;">检查</span>以及<span style="color:red;">审核</span>,一般是一个独立的过程。
|
||||
- 审计的步骤:
|
||||
- 首先启用审核策略
|
||||
- 然后对具体的资源设置审核
|
||||
- Windows系统的安全审计
|
||||
- Windows日志(系统、应用程序、安全)
|
||||
- 应用程序和服务日志(IIS日志等)
|
||||
- Linux系统的安全审计
|
||||
- 连接时间日志
|
||||
- 进程统计
|
||||
- 错误日志
|
||||
- 应用程序日志
|
||||
|
||||
#### 7、内存保护与文件系统保护
|
||||
|
||||
1. **内存保护**
|
||||
- 进程间 / 系统进程内存保护
|
||||
- 段式保护、页式保护和段页式保护
|
||||
2. **文件系统保护机制**
|
||||
- 访问控制列表
|
||||
- 加密
|
||||
- Windows (EFS、Bitlocker)
|
||||
- Linux(eCryptfs)
|
||||
|
||||
### 二、操作系统安全配置要点
|
||||
|
||||
#### 1、安装
|
||||
|
||||
- 分区设置
|
||||
- 安全补丁&最新版本
|
||||
- 官方或可靠镜像(Md5校验)
|
||||
|
||||
#### 2、最小化部署
|
||||
|
||||
- 明确需要的功能和组件,不需要的服务和功能都关闭。
|
||||
|
||||
#### 3、远程访问控制
|
||||
|
||||
- 开放端口
|
||||
|
||||
- 远程连接的限制
|
||||
|
||||
#### 4、账户策略及密码策略
|
||||
|
||||
- 管理员更名并给予安全的口令
|
||||
- 针对administrator的管理策略:
|
||||
1. Administrator管理员账户改名;
|
||||
2. 设置复杂密码;
|
||||
3. 创建名为administrator账号(陷阱账号)设置超复杂密码,禁用该账号。
|
||||
- 好的口令特点:自己容易记、别人不好猜
|
||||
- <span style="color:red;">密码策略</span>(避免弱口令)
|
||||
- 密码必须符合复杂性要求
|
||||
- 3/4原则
|
||||
- 密码长度最小值
|
||||
- 强制密码历史
|
||||
- ......
|
||||
- <span style="color:red;">帐号锁定策略</span>(应对暴力破解)
|
||||
- 帐户锁定时间
|
||||
- 帐户锁定阀值
|
||||
- 在Windows系统中,账号锁定策略对Administrator不生效,对Administrators组的其他成员生效。
|
||||
- 在Windows系统中,账号锁定策略只能保护针对非内置管理员的穷举法攻击。
|
||||
- 重置帐户锁定计数器
|
||||
|
||||
- 密码远程暴力破解
|
||||
|
||||
- 简单但有效的攻击方式;
|
||||
|
||||
- 利用人性懒惰的弱点。
|
||||
|
||||
#### 5、安全审计
|
||||
|
||||
1. **日志设置**
|
||||
|
||||
- 日志项、存储空间、访问权限
|
||||
|
||||
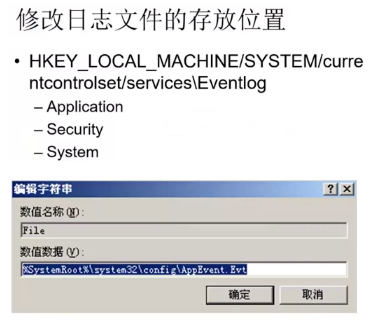
|
||||
|
||||
- 日志服务器
|
||||
|
||||
2. **其他安全设置**
|
||||
|
||||
- 安全增强软件(防病毒、主机入侵检测、安全加固软件等)
|
||||
|
||||
- 针对操作系统特性的设置
|
||||
|
||||
- Windows关闭共享、自动播放功能
|
||||
|
||||
1. 明确共享
|
||||
|
||||
2. 隐藏共享:$共享,是基于管理的目的而创建的,仅供Administrators组的成员使用。
|
||||
|
||||
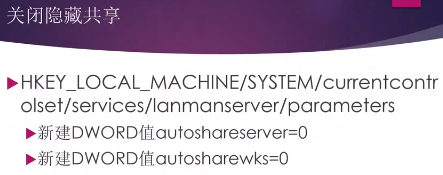
|
||||
|
||||
- Linux中默认创建文件权限等
|
||||
|
||||
### 二、操作系统安全配置要点
|
||||
Loading…
Reference in New Issue
Block a user